An out-of-band Adobe security update addressed critical flaws in Photoshop, Acrobat Reader and other products.
Adobe has released out-of-band updates addressing critical vulnerabilities in its Photoshop and Acrobat Reader products, which if exploited could allow arbitrary code-execution.
Overall, Adobe on Wednesday patched flaws tied to 41 CVEs across its products, 29 of which were critical in severity. The fixes were released outside of Adobe’s regularly scheduled update day, which was earlier in March (during which, in fact, Adobe had no patches).
In this most recent group, Adobe Photoshop had the most vulnerabilities fixed, with 22 CVEs addressed overall, 16 of which were critical: “Adobe has released updates for Photoshop for Windows and macOS. These updates resolve multiple critical and important vulnerabilities,” according to Adobe’s advisory. “Successful exploitation could lead to arbitrary code-execution in the context of the current user.”
Critical arbitrary execution vulnerabilities include heap corruption (CVE-2020-3783), memory corruptions (CVE-2020-3784, CVE-2020-3785, CVE-2020-3786, CVE-2020-3787, CVE-2020-3788, CVE-2020-3789, CVE-2020-3790), out of bounds writes (CVE-2020-3773, CVE-2020-3779) and buffer errors (CVE-2020-3770, CVE-2020-3772, CVE-2020-3774, CVE-2020-3775, CVE-2020-3776, CVE-2020-3780).
Affected are Photoshop CC 2019 (versions 20.0.8 and earlier) and Photoshop 2020 (21.1 and earlier) for Windows and macOS. Users can update to Photoshop CC 2019 versions 20.0.9 and Photoshop 2020 21.1.1.
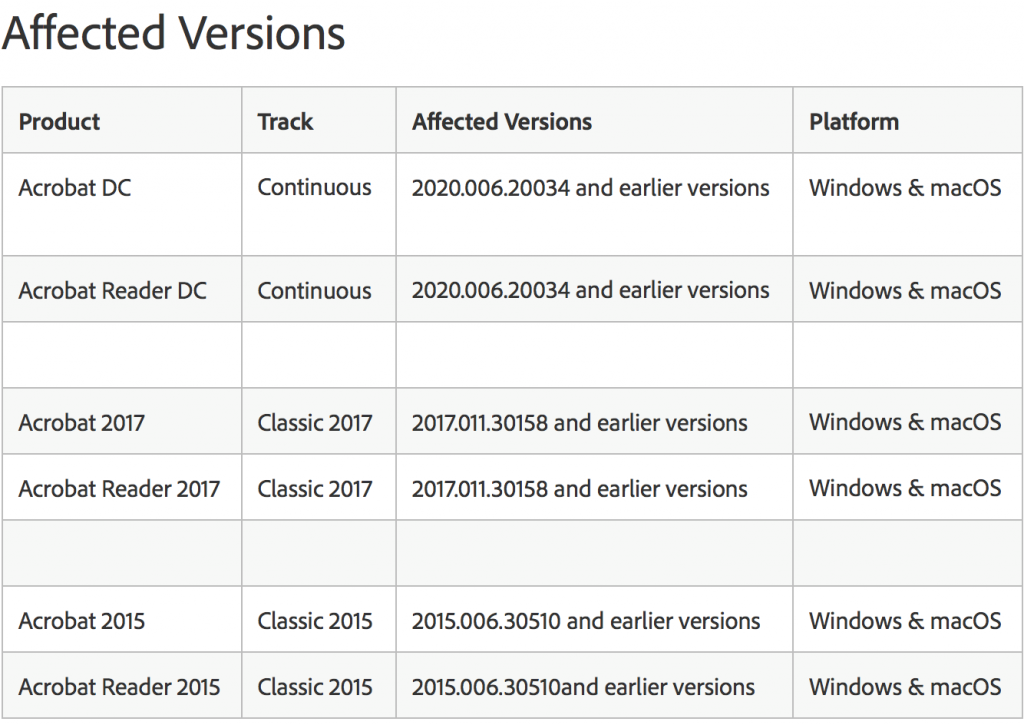
Adobe also addressed 13 vulnerabilities in Acrobat and Reader, including nine critical flaws. Critical flaws include out-of-bounds write (CVE-2020-3795), stack based buffer overflow (CVE-2020-3799), use-after-free bugs (CVE-2020-3792, CVE-2020-3793, CVE-2020-3801, CVE-2020-3802, CVE-2020-3805), buffer overflow (CVE-2020-3807) and memory corruption (CVE-2020-3797). All of these critical flaws enable arbitrary code execution in the context of the current user, according to Adobe.
Below are the affected versions of Acrobat and Reader; Adobe urges users to update to the fixed versions (2020.006.20042 for Acrobat and Reader DC, 2017.011.30166 for Acrobat and Reader 2017, and 2015.006.30518 for Acrobat and Reader 2015).
Other vulnerabilities include two critical flaws in Adobe ColdFusion, including a remote file read (CVE-2020-3761) from the ColdFusion install directory; and a critical file inclusion flaw (CVE-2020-3794) enabling arbitrary code execution of files located in the webroot or subdirectory.
Two critical flaws were also rooted out in Adobe Bridge that could enable arbitrary code execution, including an out-of-bounds write flaw (CVE-2020-9551) and heap based buffer overflow glitch (CVE-2020-9552). And, Adobe also patched important severity flaws in its Adobe Genuine Integrity Service and Adobe Experience Manager.
While Adobe had no regularly scheduled updates earlier in March, it did stomp out flaws tied to 42 CVEs in its regularly scheduled February updates, with 35 of those flaws being critical in severity. That well trumped Adobe’s January security update, which addressed just nine vulnerabilities overall, including ones in Adobe Illustrator CC and Adobe Experience Manager.
Interested in security for the Internet of Things and how 5G will change things? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.



0 Commentaires