Adobe patched 36 flaws, including critical vulnerabilities in Acrobat and Reader and its DNG Software Development Kit.
Adobe has fixed 16 critical flaws across its Acrobat and Reader applications and its Adobe Digital Negative (DNG) Software Development Kit. If exploited, the flaws could lead to remote code execution.
Overall, Adobe fixed vulnerabilities tied to 36 CVEs in its regularly-scheduled Tuesday security update. Those include 24 critical- and important-severity flaws in its Acrobat and Reader application, used for creating and managing PDF files, and 12 in its Adobe DNG Software Development Kit (SDK), which provides support for reading and writing DNG files used for digital photography.
“Adobe is not aware of any exploits in the wild for any of the issues addressed in these updates,” according to Adobe’s Tuesday alert.
Acrobat and Reader
Twelve critical flaws were fixed in Acrobat and Reader. The majority of these, if exploited, can allow an attacker to launch arbitrary code execution attacks.
The flaws include a heap-based buffer overflow flaw (CVE-2020-9612) that exists within the processing of JPEG2000 images, Dustin Childs, manager at Trend Micro’s Zero Day Initiative, told Threatpost.
“The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a heap-based buffer,” Childs said. “An attacker can leverage this vulnerability to execute code in the context of the current process.”
Another code-execution flaw of note is a out-of-bounds write glitch (CVE-2020-9597). Childs said this specific bug exists within the parsing of .JPEG files. “Crafted data in a JPEG file can trigger a write past the end of an allocated buffer,” he said. “An attacker can leverage this vulnerability to execute code in the context of the current process.”
Also of note is a flaw stemming from a specific JavaScript code embedded in a PDF file, which can lead to heap corruption (CVE-2020-9607) when opening a PDF document in Adobe Acrobat Reader DC 2020.006.20034.
“With careful memory manipulation, this can lead to arbitrary code execution,” said Cisco Talos researchers who discovered the flaw in a Tuesday analysis. “The victim would need to open the malicious file or access a malicious web page to trigger this vulnerability.”
The remaining critical flaws enabling code execution include another out-of-bounds write glitch (CVE-2020-9594), buffer errors (CVE-2020-9605, CVE-2020-9604) and another use-after-free flaw (CVE-2020-9606). Adobe also addressed a critical race condition flaw (CVE-2020-9615) and security bypass flaws (CVE-2020-9614, CVE-2020-9613, CVE-2020-9596, CVE-2020-9592), which can be exploited by a bad actor to bypass security restrictions features.
“These updates address multiple critical and important vulnerabilities,” according to Adobe’s alert. “Successful exploitation could lead to arbitrary code execution in the context of the current user.”
A number of important-severity flaws were also patched, including a null pointer (CVE-2020-9610) and stack exhaustion (CVE-2020-9611) flaw, which can allow bad actors to launch denial-of-service attacks against the application. Out-of-bounds read flaws (CVE-2020-9609, CVE-2020-9608, CVE-2020-9603, CVE-2020-9602, CVE-2020-9601, CVE-2020-9600, CVE-2020-9599) and invalid memory access flaws (CVE-2020-9598, CVE-2020-9595, CVE-2020-9593) were also patched, which could be abused to access sensitive information.
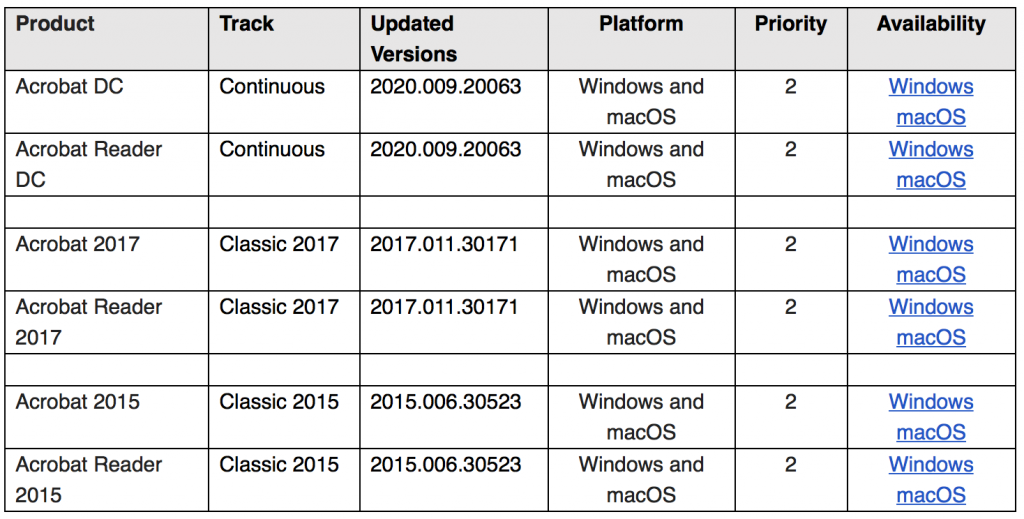
Affected are Acrobat and Reader DC Continuous versions 2020.006.20042 and earlier; Acrobat and Reader Classic 2017 versions 2017.011.30166 and earlier; and Acrobat and Reader Classic 2015 versions 2015.006.30518 and earlier. The patched versions for each affected product is below.
Adobe had released a pre-notification security advisory for the Acrobat and Reader updates last week.
Adobe DNG SDK
Adobe also issued patches for flaws in versions 1.5 and earlier of its DNG SDK. Users are urged to update to version 1.5.1 of the SDK.
This includes critical heap overflow flaws tied to four CVEs (CVE-2020-9589, CVE-2020-9590, CVE-2020-9620, CVE-2020-9621). If exploited, the flaws could enable remote code execution.
Also patched were eight out-of-bounds read flaws (CVE-2020-9622, CVE-2020-9623, CVE-2020-9624, CVE-2020-9625, CVE-2020-9626, CVE-2020-9627, CVE-2020-9628, CVE-2020-9629) that could be abused for information disclosure. Mateusz Jurczyk with Google Project Zero was credited with discovering the flaws.
In April, Adobe released security patches for vulnerabilities in its ColdFusion, After Effects and Digital Editions applications. If exploited, the flaws could enable attackers to view sensitive data, gain escalated privileges, and launch denial-of-service attacks. Also in April, Adobe released an out-of-band patch addressing critical flaws in Adobe Bridge, Adobe Illustrator and the Magento e-commerce platform. If exploited, the most severe vulnerabilities could enable remote code execution on affected systems.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.


0 Commentaires