As people increasingly work from home and online communication platforms such as Zoom explode in popularity in the wake of coronavirus outbreak, cybercriminals are taking advantage of the spike in usage by registering new fake “Zoom” domains and malicious “Zoom” executable files in an attempt to trick people into downloading malware on their devices.
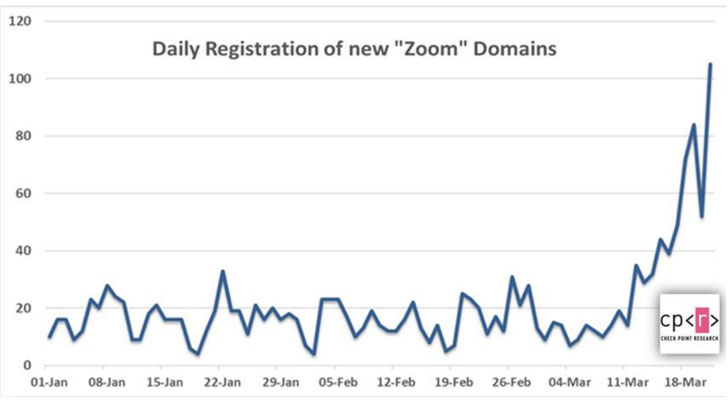
According to a report published by Check Point and shared with The Hacker News, over 1,700 new “Zoom” domains have been registered since the onset of the pandemic, with 25 percent of the domains registered in the past seven days alone.
“We see a sharp rise in the number of ‘Zoom’ domains being registered, especially in the last week,” said Omer Dembinsky, Manager of Cyber Research at Check Point.
“The recent, staggering increase means that hackers have taken notice of the work-from-home paradigm shift that COVID-19 has forced, and they see it as an opportunity to deceive, lure, and exploit. Each time you get a Zoom link or document messaged or forwarded to you, I’d take an extra look to make sure it’s not a trap.”
With over 74,000 customers and 13 million monthly active users, Zoom is one of the most popular cloud-based enterprise communication platforms that offers chat, video and audio conferencing, and options to host webinars and virtual meetings online.
The popularity of Zoom has shot up significantly in recent weeks as millions of students, business people, and even government employees across the world are forced to work and socialize from home during the coronavirus pandemic.
The report comes following a significant increase in the number of malicious coronavirus-related domains, with bad actors finding new ways to profit off the global health concern to stage a variety of malware attacks, phishing campaigns, and create scam sites and malicious tracker apps.
What’s more, the researchers said they detected malicious files with the name “zoom-us-zoom_##########.exe,” which when executed, installed potentially unwanted programs (PUPs) such as InstallCore, a dodgy bundleware application that’s known to install other kinds of malware.
But Zoom is not the only app to be targeted by cybercriminals. With schools turning to online learning platforms to keep students occupied, Check Point researchers said they also discovered phishing sites masquerading as the legitimate Google Classroom (e.g., googloclassroom.com and googieclassroom.com) website to trick unwitting users into downloading malware.
Zoom Fixes Privacy Issue in Its iOS App
Zoom, for its part, has had its share of privacy and security issues too. Last year, the video conferencing app fixed a vulnerability that could let websites hijack users’ webcam and “forcibly” join them to a Zoom call without their permission.
Then earlier this January, the company squashed another bug that could have allowed attackers to guess a meeting ID and join an unprotected meeting, potentially exposing private audio, video, and documents shared throughout the session. Following the disclosure, Zoom introduced default passwords for each meeting that participants need to enter when joining by manually entering the meeting ID.
And finally, just over the weekend, Zoom updated its iOS app after it was caught sending device information and a unique advertiser identifier to Facebook using the social network’s software development kit (SDKs) and concerns were raised over its failure to disclose the data sharing in its privacy policy.
Highlighting some of the privacy risks associated with using Zoom’s products, The Electronic Frontier Foundation (EFF) said hosts of Zoom calls can see if participants have the Zoom video window active or not to track if they are paying attention. Administrators can also see the IP address, location data, and device information of each participant.
To safeguard yourself from such threats, it’s essential that the apps are kept up-to-date, and be on the lookout for emails from unknown senders and lookalike domains that contain spelling errors.
Besides this, also don’t open unknown attachments or click on promotional links in the emails, the cure for Corona will not arrive via email, and also ensure you’re ordering goods from only authentic sources.



0 Commentaires