Adobe fixed critical flaws in Illustrator, Magento and Bridge in an out-of-band security update.
Adobe is warning of critical flaws in Adobe Bridge, Adobe Illustrator and the Magento e-commerce platform. If exploited, the most severe vulnerabilities could enable remote code execution on affected systems.
Adobe’s out-of-band security update, released on Tuesday, addressed vulnerabilities tied to 35 CVEs overall (25 of which were critical). The majority of these flaws affect Adobe Bridge (version 10.0.1 and earlier for Windows), the company’s digital asset management software.
“This update addresses multiple critical and important vulnerabilities that could lead to arbitrary code execution and information disclosure in the context of the current user,” according to Adobe’s update.
Critical flaws include a stack-based buffer overflow flaw (CVE-2020-9555), heap overflow bugs (CVE-2020-9562, CVE-2020-9563), memory corruption glitch (CVE-2020-9568) and use-after-free vulnerabilities (CVE-2020-9566, CVE-2020-9567). Also included are critical out-of-bounds write flaws (CVE-2020-9554, CVE-2020-9556, CVE-2020-9559, CVE-2020-9560, CVE-2020-9561, CVE-2020-9564, CVE-2020-9565, CVE-2020-9569). All of these could enable arbitrary code execution if exploited by a remote attacker.
“There are several Critical-rated CVEs being addressed that could allow a remote attacker to execute code on a system if a user opened a specially crafted file,” Dustin Childs, manager at Trend Micro’s Zero Day Initiative, told Threatpost. “Of these, the out-of-bound writes and heap overflows should be considered more critical than the others. Still, all of these bugs require a significant amount of work to exploit since an attack has no trivial way of controlling the heap.”
Adobe also disclosed three “important” severity out-of-bounds read flaws (CVE-2020-9553, CVE-2020-9557, CVE-2020-9558) in Adobe Bridge that could enable information disclosure. Francis Provencher, Mat Powell and an anonymous reporter were credited for discovering the flaws, all working with Trend Micro’s Zero Day Initiative.
Users are urged to update to Adobe Bridge version 10.0.4 for Windows and macOS. The update is a “priority 3,” which according to Adobe “resolves vulnerabilities in a product that has historically not been a target for attackers.”
Also affected is Adobe Illustrator 2020 (versions 24.0.2 and earlier) for Windows. Adobe’s vector graphics editor application had critical memory corruption vulnerabilities (CVE-2020-9570, CVE-2020-9571, CVE-2020-9572, CVE-2020-9573, CVE-2020-9574) that could enable arbitrary code execution if exploited.
The vulnerabilities were been fixed in Illustrator 2020 24.1.2 for Windows in a “priority 3” patch. Kushal Arvind Shah of Fortinet’s FortiGuard Labs was credited with reporting the flaws.
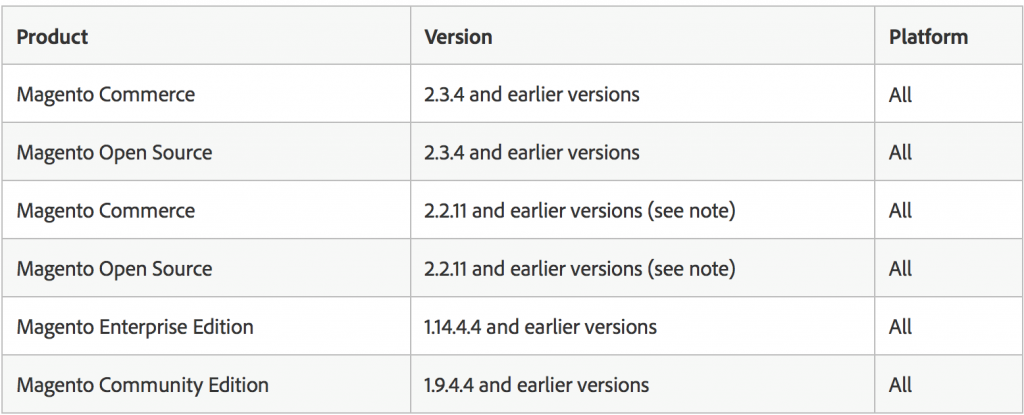
Adobe also patched several critical flaws in Magento – a favorite target of the Magecart cybergang – that if exploited could lead to arbitrary code execution or information disclosure. The most serious of these include critical command infection flaws (CVE-2020-9576, CVE-2020-9578, CVE-2020-9582, CVE-2020-9583) and critical security mitigation bypass vulnerabilities (CVE-2020-9579, CVE-2020-9580). Below are affected Magento versions.
Earlier this month, Adobe released its regularly scheduled security patches for vulnerabilities in its ColdFusion, After Effects and Digital Editions applications. If exploited, the flaws could enable attackers to view sensitive data, gain escalated privileges, and launch denial-of-service attacks. Each of the bugs were rated important-severity, based on CVSS rankings, marking an extremely low-volume month for Adobe bug fixes.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.



0 Commentaires