Thanks to WFH, IoT refrigerators, Samsung TVs and more can now be back-channel proxies into the corporate network.
The work-from-home (WFH) paradigm that has become the new normal in the age of coronavirus comes with exacerbated network security risk – as evidenced by growing a number of botnets and automated attacks that are taking advantage of known vulnerabilities in both consumer and corporate IT gear. The situation is forcing IT to adopt new strategies to gain visibility into their network environments.
According to Nate Warfield, senior security program manager at Microsoft, new vulnerabilities found in network and Internet-of-Things (IoT) equipment are being weaponized by cybercriminals within days of disclosure – and sometimes hours. And the attack surface continues to widen tremendously since most office jobs have been reconfigured into telecommuting positions.
“If your job is to take care of the security of an enterprise network, your network perimeter just got really big,” he said, speaking at Tuesday’s SAS@home virtual security conference. “It has now expanded to all of your home users, all of their house-wide networks and devices, as well as what you’ve already known that you have to take care of.”
The New Normal: Home + Enterprise Threat Surface
This can include IoT gadgets that are typically not counted in the corporate footprint, he noted: “We’re talking old routers, unpatched routers, possibly hacked routers – but also Samsung Smart TVs and that IoT refrigerator that everybody thought was so cool. Yeah, that’s also on your corporate network now, because it’s connected to your home user’s network and therefore is now a possible proxy back into your corporate network.”
Microsoft’s Nate Warfield, speaking at SAS@home.
The issue of course is that consumer-grade devices and commodity hardware can suffer from a lack of security-by-design, with issues like default passwords that consumers don’t know to change, as well as security vulnerabilities.
“But you know, I’m sure all of your users remembered to change their refrigerator passwords, because you know the FBI was nice enough to warn all of us to do it,” Warfield said.
Using tools like the Shodan search engine, Warfield pointed out that it’s a trivial matter to uncover vulnerable devices, many of which are using basic HTTP authentication, no SSL encryption and no two-factor authentication.
“All of the IoT and home media devices are all things you can find on Shodan right now, with just a quick search,” he said.
Adding insult to injury, even enterprise equipment isn’t necessarily always fully tested, patched and kept up to date. Warfield noted that as of Tuesday there are still 126,000 machines for instance that haven’t been patched for the SMB “Ghost” vulnerability that Microsoft fixed in March. “These are all out there just waiting to get hit,” Warfield said.
And, IT is doing more remote administration thanks to WFH. “IT staff can’t walk into a data center to reset a server, and they need to be able to connect to it, so they use remote access,” Warfield explained. “Well, you can find those things on Shodan as well. Hopefully everybody’s using a strong password, but these are all entry points into your network that are more vulnerable now because nobody’s in the office.”
New Approaches for IT Threat-Hunting
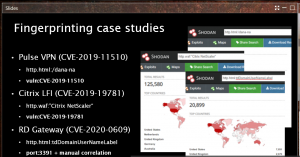
The Citrix NetScaler local file inclusion vulnerability disclosed in December provides an object lesson for how quickly adversaries are moving to automate new exploits, Warfield noted.
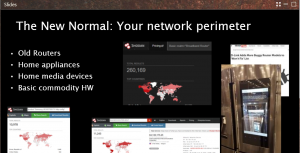
The new network perimeter — click to enlarge.
“Basically, this bug allowed people to hack into a VPN device, a very expensive VPN device,” he said. “And you know what happens if you hack a VPN device – it’s got connectivity to your entire corporate network and the keys to the kingdom. This vulnerability didn’t require any special coding to exploit – there was no ASLR or anything to bypass – [the exploit] was just a curl command sent to a specific path on the NetScaler device. [Telemetry] picked up people already throwing automated payloads trying to exploit this thing within two days. We’re not even talking advanced attackers – this was script kiddies who put this into automated systems in two days.”
To combat such swiftly moving attacks, even across the expanded WFH attack surface, Warfield noted that open-source threat intelligence tools like GreyNoise – and also Shodan itself – can be invaluable.
“GreyNoise is basically a sensor network that picks up indiscriminate scanning, mostly botnets, brute-forcing attempts, and things that are sort of just spraying the internet with traffic, either port scans or throwing payloads,” Warfield explained. “It’s not going to pick up targeted attacks, because usually attackers are smarter than to spray high-value exploits at hundreds of thousands or millions of IPs. But what’s interesting is you can start pulling metrics data.”
Security staff can search for suspicious activity in a variety of ranges, from the country level all the way down to a specific network range that would be relevant to a specific business. In this way, it’s possible to flag devices that may be compromised and used in a botnet, for example.
“We discovered that all the way down in Antarctica there’s one machine that’s out there spraying malicious payloads around, which is kind of interesting,” the researcher noted.
Shodan offers the ability to perform scans on one’s newly expanded consumer footprint – provided that the IT staff has an inventory of where its users are on the web.
“We want to build lists of IPs, you know once you figure out where users are coming from, so you can start looking and say hey, are they using any of these different types of devices – things that have been reported as vulnerable or unsupported old routers for instance,” Warfield said, adding that Shodan uses metadata that it refers to as “facets” as search parameters.
“So you can say, hey give me the stats for the specific facet of the metadata that I want, within your range, or use ‘net:0/0′ which is shorthand for the entire internet,” he explained.
To uncover possibly problematic devices within home users’ footprints, SSL certificate data can be useful, according to Warfield.
“A lot of your out-of-the-box solutions, a lot of your SoHo routers and a lot of your IoT stuff will generate a new SSL certificate [for each installation], but all of the issuer information is going to be the same,” he explained. “And once you figure out what that is, you can then go and look for the issuer common name [i.e., a common router type] and…you would say, now I’m going to restrict it down by my autonomous system or my IP networks [to see if any of those devices are in your footprint].”
Even more useful, Shodan allows paid users to look for known bugs. “The ability to search for vulnerabilities is locked behind either the corporate or the enterprise licenses on Shodan, which are very expensive and out of the range of your average script kiddie. But it’s very affordable for the corporate environment,” Warfield said.
Fingerprinting Corporate Risk
The bottom line is that attacks on enterprises are changing thanks to the growing enterprise/home hybrid IT profile that many businesses now have – and opportunities for compromise are growing.
“Attackers thrive on chaos, and there’s no more chaotic time on the internet or in our lives than right now,” Warfield said. “We’re all here in our houses, your network perimeter is changed, and it’s likely that your perimeter is going to be changed for the foreseeable future – and possibly forever. The new normal may be that a majority of the workforce is working remote and attackers know that. They’re going to be very smart and very, very crafty, and they’re going to go after your home users to try to back-channel into your corporate network. They’ll find the low-hanging fruit. And a lot of this stuff isn’t just low-hanging – more like it’s fallen off and is rotting on the ground.”
Thus, it’s important that IT security teams assess their networks regularly, using some of the tools that have historically not been within their purview.
“GreyNoise and Shodan both are ways to keep tabs,” Warfield said. “You can tell GreyNoise to alert you if your IP network starts sending weird or malicious traffic or doing something bizarre for instance.”
“This is something you may have to do as you’re trying to figure out what networks these people on your VPNs are coming from,” he added. “You have to remap the perimeter based on where your remote users are coming from, so it’s just more network intelligence work. You need to have more tools than just the things that you’ve always thought of.”
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.



0 Commentaires