Several flaws found in Nvidia’s graphics drivers could enable denial of service, code execution and other malicious attacks.
Nvidia issued patches for high-severity vulnerabilities in its graphics driver, which can be exploited by a local attacker to launch denial-of-service (DoS) or code-execution attacks.
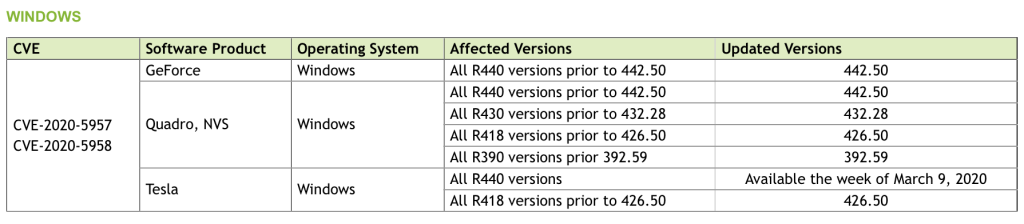
Nvidia’s graphics processing unit (GPU) display driver is used in devices targeted for enthusiast gamers; it’s the software component that enables the device’s operating system and programs to use its high-level graphics hardware. Specifically impacted are display drivers used in GeForce, Quadro and Tesla-branded GPUs for Windows.
The most severe flaw exists in the control panel component of the graphics driver, which is a utility program helping users monitor and adjust the settings of their graphics adapter. According to Nvidia in its security advisory, published Friday, an attacker with local system access can corrupt a system file in the control panel, which would lead to DoS or escalation of privileges.
The vulnerability (CVE‑2020‑5957) ranks 8.4 out of 10.0 on the CVSS scale, making it high-severity.
Another vulnerability, this one medium-severity, exists in the control panel of the graphics driver (CVE‑2020‑5958). An attacker with local system access could exploit this flaw by planting a malicious dynamic link library (DLL) file in the control panel, which may lead to code execution, DoS or information disclosure.
For both flaws in the graphics driver, the affected versions and subsequent patched versions are listed below. Patched versions are now available, with the exception of a patch for vulnerable R440 versions of Tesla for Windows; fixes for that will be available on the week of March 9.
Nvidia also disclosed several vulnerabilities in the Virtual GPU (vGPU) Manager, its tool that enables multiple virtual machines to have simultaneous, direct access to a single physical GPU, while also using Nvidia graphics drivers deployed on non-virtualized operating systems.
The most severe of these flaws exists in the vGPU plugin, “in which an input index value is incorrectly validated, which may lead to denial of service,” according to Nvidia. The vulnerability (CVE‑2020‑5959) is 7.8 out of 10.0 on the CVSS scale, making it high-severity.
Another medium-severity flaw (CVE-2020-5960) in vGPU stems from the tool’s kernel mode (nvidia.ko) which is vulnerable to a null pointer dereference error. This type of error occurs when a program attempts to read or write to memory with a null pointer, causing a segmentation fault. The flaw can lead to denial of service, according to Nvidia.
Nvidia also addressed a medium-severity vulnerability in its vGPU graphics driver for guest operating systems. An “incorrect resource clean up on a failure path” in this driver can impact the guest virtual machine, leading to denial of service. A variety of versions are affected for these vGPU software flaws (they can be found here); Nvidia said that updated versions are upcoming in March.
It’s only the latest Nvidia security patch impacting its gaming-enthusiast customer base. Nvidia last year issued fixes for high-severity flaws in two popular gaming products, including its graphics driver for Windows and GeForce Experience. The flaws could be exploited to launch an array of malicious attacks – from DoS to escalation of privileges. Also in 2019, Nvidia patched another high-severity vulnerability in its GeForce Experience software, which could lead to code-execution or DoS of products, if exploited.



0 Commentaires