
Cisco’s IOS XE software for SD-WAN routers has a high-severity insufficient input validation flaw.
Cisco has patched a high-severity vulnerability in its router software, which if exploited could enable a local, authenticated attacker to execute arbitrary commands with root privileges.
The flaw exists in Cisco IOS XE. This Linux-based version of Cisco’s Internetworking Operating System (IOS) is used in Cisco software-defined wide area network (SD-WAN) routers. Affected routers include the Aggregation Services Routers (ASR) 1000 models, Integrated Services Routers (ISR) 1000 models, ISR 4000 models and Cloud Services Router 1000V models. These are all used by small businesses and enterprises alike.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability,” according to Cisco’s Wednesday advisory.
The flaw exists in the command line interface (CLI) utility of Cisco IOX XE, used to configure the network device. The CLI does not sufficiently validate input commands. An attacker could exploit this vulnerability by authenticating to the device and submitting a crafted input to the CLI utility, according to Cisco.
“The attacker must be authenticated to access the CLI utility,” according to Cisco. “A successful exploit could allow the attacker to execute commands with root privileges.”
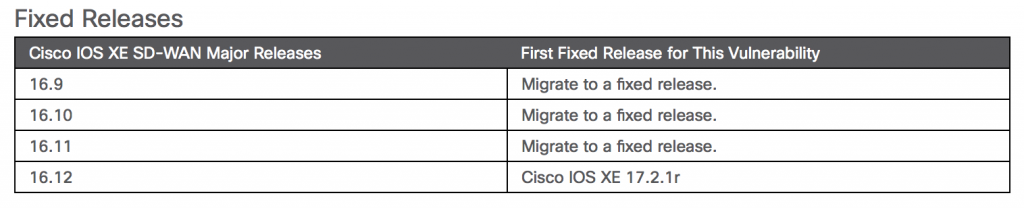
The flaw (CVE-2019-16011) has a CVSS 3.0 score of 7.8 out of 10, which makes it high severity. Fixed releases for Cisco IOS XE SD-WAN are below.
Julien Legras and Thomas Etrillard of Synacktiv were credited for reporting the flaw.
Cisco’s IOS XE software has had its fair share of security issues. In March, Cisco issued 24 patches tied to vulnerabilities in its IOS XE operating system. The networking giant in January also released fixes for another high-severity glitch in the web user interface of Cisco IOS and Cisco IOS XE Software.
Last July, Cisco patched a high-severity vulnerability in IOS XE, which could enable a remote attacker to reconfigure or execute commands on impacted devices. And in August, a critical remote authentication-bypass vulnerability – with the highest possible severity level of 10 out of 10 on the CvSS scale – was found in the Cisco REST API virtual service container for Cisco IOS XE Software.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.
Also, don’t miss our latest on-demand webinar from DivvyCloud and Threatpost, A Practical Guide to Securing the Cloud in the Face of Crisis, with critical, advanced takeaways on how to avoid cloud disruption and chaos.



0 Commentaires