APT34/OilRig and APT33/Elfin have established a highly developed and persistent infrastructure that could be converted to distribute destructive wiper malware.
Two Iran-backed APTs could be working together on a sprawling, three-year campaign to compromise high-value organizations from the IT, telecom, oil and gas, aviation, government and security sectors in Israel and around the world, according to a report by researchers at ClearSky.
They maintain, APT34/OilRig and APT33/Elfin appear to be linked to the campaign (which they dubbed Fox Kitten). The offensive has resulted in the establishment of a highly developed and persistent infrastructure of access to company networks, which has been used for reconnaissance and espionage, they said. However, it’s also the perfect launchpad for the deployment of destructive malware such as ZeroCleare and Dustman, researchers noted, both of which have been linked to the APTs.
“Aside from malware, the campaign enfolds an entire infrastructure dedicated to ensuring the long-lasting capability to control and fully access the targets chosen by the Iranians,” researchers said in an analysis over the weekend.
According to the analysis, Fox Kitten’s objective has been to develop and maintain access routes to the targeted organizations, establishing persistent footholds within them; stealing information; and pivoting from within to additional targets via supply-chain attacks.
The Fox Kitten Toolset
The campaign has used a range of tools, including some based on open-source code and some custom weapons.
The initial infection vector has been the exploitation of recently disclosed vulnerabilities in different VPN services such as Pulse Secure VPN, Fortinet VPN and Global Protect by Palo Alto Networks.
“We assess this attack vector to be significant also in 2020 apparently by exploiting new vulnerabilities in VPNs and other remote systems (such as the latest one existing in Citrix),” according to the report. “Iranian APT groups have developed good technical offensive capabilities and are able to exploit ‘one-day’ vulnerabilities in relatively short periods of time, starting from several hours to a week or two.”
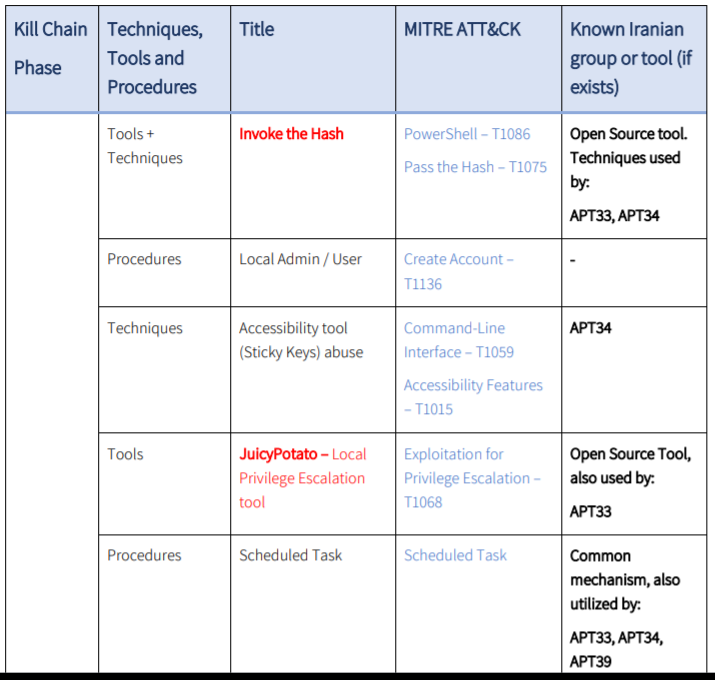
Upon gaining foothold at the target, the attackers tried to maintain the access to the networks via a variety of communication tools, including opening Remote Desktop (RDP) links over SSH tunneling, in order to camouflage and encrypt the communication with the targets. They also installed a set of remote access and communication tools and tools designed for privilege escalation; along with several backdoors into the systems they have compromised.
The use of VPNs and RDP is savvy, the researchers noted: “The time needed to identify an attacker on a compromised network is long, and varies between months to not at all. The existing monitoring capability for organizations to identify and block an attacker that entered through remote communication tools is difficult, to impossible.”
At the final stage, after successfully infiltrating the organization, the attackers “performed a routine process of identification, examination and filtering of sensitive, valuable information from every targeted organization,” according to the report. “The valuable information was sent back to the attackers for reconnaissance, espionage or further infection of connected networks.”
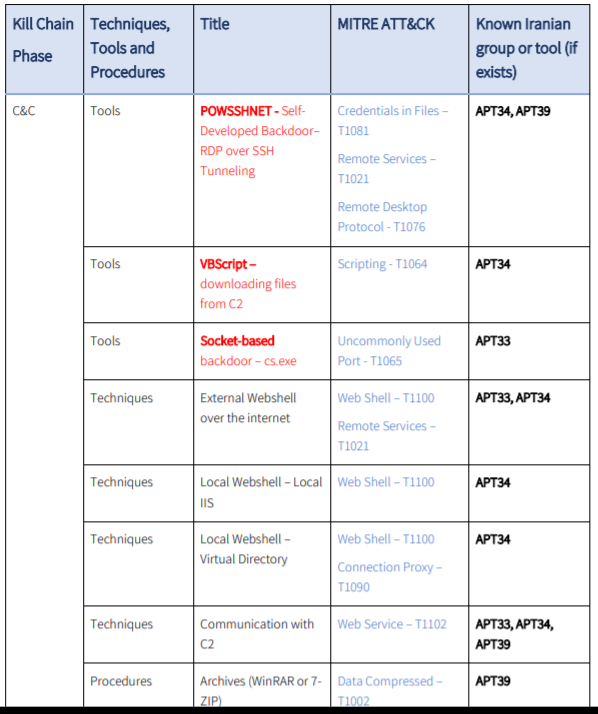
ClearSky said that the custom tools used by the Iranian attackers include the backdoor that opens a SSH tunnel between the attacker and the target, and allows the former to connect to the latter through RDP. This is called POWSSHNET. Other self-developed tools include a database- and open-ports-mapping tool called STSRCheck; a VBScript that can download TXT files from the command-and-control (C2) server and unify these files to a portable executable file; a backdoor executable file used to open a socket-based connection to a hardcoded IP address; and an executable “Port.exe” tool to scan predefined ports and IP addresses.
The attackers tailored their custom tools to match the operating systems at target organizations. “Thus, in 2017 the tools were developed and fitted to 32-bit systems, while in 2019 the tools were developed for 64-bit systems,” according to the analysis.
Open source-based tools adjusted to the attackers’ use include PowerShell commands in order to perform “Pass the Hash” methods; JuicyPotato, a local privilege escalation tool; Ngrok, FRP and Serveo for C2 protocol; and Putty and Plink, for remote services.
The easiest protection point in the kill chain is clearly via timely patching, researchers note.
“Several VPN products have had vulnerabilities disclosed in recent months, and so it’s not surprising that state-backed groups are looking to leverage their window of opportunity, knowing all too well that patching vulnerable systems can take organizations a long time,” Javvad Malik, security awareness advocate at KnowBe4, said via email. “There is a certain irony to this as organizations that deploy VPNs for security, could be breached because of those very security products. Because many security products run at higher privileges, any compromise could give a criminal the keys to the kingdom. Therefore it would be prudent for organizations to identify security software in their asset inventories, and ensure they are patched as a matter of urgency.”
Attribution
The researchers said that they have “medium-high” confidence that APT34/OilRig is involved in the campaign; and “medium” confidence that APT33/Elfin is.
The APT34 connection stems from the fact that part of the attack infrastructure used by the group in previous campaigns has been reused for Fox Kitten. And, several of the targets are the same targets that the group has gone after before. Also, the infrastructure contains widespread use of webshells, which fits the group’s past tactics, techniques and procedures (TTPs).
“In April-May 2019, a number of webshells belonging to OilRig were revealed throughout the Middle East, most of which against companies in the Gulf and in Israel – in Israel, a webshell-based attack was revealed in one of the country’s leading universities, while in the Gulf several webshells were found in aviation companies and ministries,” explained the researchers.
A further connection comes from the ZeroCleare malware attacks, which were likely the work of APT34/OilRig, according to IBM X-Force researchers. ZeroCleare is a destructive wiper malware that last year was deployed to target the energy and industrial sectors in the Middle East; it shares characteristics with the infamous Shamoon malware. The same vulnerabilities that the group exploited for the ZeroCleare attacks were targeted in Fox Kitten, ClearSky researchers noted.
They also saw an overlap in approaches with the APT39/Chafer group, considered a subgroup of APT34/OilRig. “The most apparent overlap in methods includes the use of stolen VPN credentials, lateral movement through RDP, and exfiltration based on file compression in ZIP or RAR formats,” according to the report.
As for APT33/Elfin, APT34/OilRig likely collaborated on the actual destructive malware portion of the ZeroCleare campaign with APT33/Elfin, IBM X-Force researchers found.
“IBM has attributed the ZeroCleare distribution campaign to APT34 with an additional Iranian group known for [destructive] capabilities, and we assess that this means APT33,” according to ClearSky. “It was mentioned that the attack was divided into two main parts – breach and access to the network be APT34, and then distribution of a destructive capability by another Iranian group, which we assess to be APT33.”
Also, security firm Dragos recently observed an offshoot of APT33, dubbed Magnallium, expanding its targeting from the global oil-and-gas industry to specifically include electric companies in North America. Researchers there called that campaign “Parisite” – and ClearSky researchers said that Parisite is in fact just one part of the broader Fox Kitten campaign. This is based on overlaps between some of the files used in the Parisite campaign and the files and tools used in the Fox Kitten campaign, they said.
“[Our research] reveals a strong connection to two groups that were [previously] analyzed as separate units. In recent months, several reports dealing with tools common to APT34 and APT33 were published, while [our] report exemplifies the cooperation between the two as one big espionage establishment,” according to ClearSky. “We know that both groups work in many tracks – infection and social engineering, reconnaissance and espionage, and even sabotage, while emphasizing each group’s specialty.”
While no destructive malware has been seen in the Fox Kitten campaign, ClearSky noted that it would be very easy to use the infrastructure to disseminate a wiper on a large scale. And given the connections to ZeroCleare, the concern becomes more relevant.
“We assess such recon campaigns to be convertible to disseminate destructive attacks after studying the target organization, similar to the ZeroCleare events in the Gulf,” according to the analysis.
Here are some of the TTP overlaps observed by the research firm:
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.





0 Commentaires