Researchers warn that Keeper, using Magecart code, will launch increasingly sophisticated attacks against online merchants worldwide in the coming months.
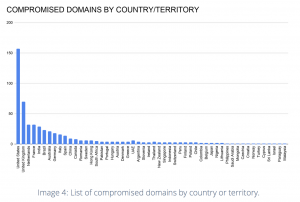
Since its launch three years ago, the Keeper threat group has compromised more than 570 e-commerce websites, from online liquor stores to Apple product resellers. And experts warn of future, increasingly sophisticated attacks against online merchants worldwide.
The Keeper group, a faction of the Magecart umbrella, consists of an interconnected network of 64 attacker domains and 73 exfiltration domains. Researchers recently uncovered an unsecured access log on the Keeper control panel harboring 184,000 compromised payment cards, which had time stamps that ranged from July 2018 to April 2019.
“Extrapolating the number of cards per nine months to Keeper’s overall lifespan, and given the dark-web median price of $10 per compromised card-not-present (CNP) card, this group has likely generated upwards of $7 million USD from selling compromised payment cards,” according to new research from Gemini Advisory on Tuesday.
As is common for Magecart groups, Keeper attackers launched attacks by breaking into online store backends, altering their source code and inserting malicious scripts that log payment-card details entered by shoppers in checkout forms. Researchers say Keeper exfiltration and attacker domains use identical login panels and are all linked to the same dedicated server. This server hosts both the malicious payload and the exfiltrated data stolen from victim sites, they said.
“The Gemini team has named this group ‘Keeper’ based on its repeated usage of a single domain called fileskeeper[.]org to inject malicious payment card-stealing JavaScript (JS) into the website’s HTML code, as well as receive compromised card data,” said researchers.
Victimology
The 570 victim e-commerce stores range from small boutique shops to top sites in the Alexa Global Rankings, receiving between 500,000 to 1 million visitors monthly. Examples include an India-based online jewelry store (ejohri[.]com), a U.S. based premier wine and spirits seller (cwspirits[.]com) and an Indonesia-based Apple product reseller (ibox.co[.]id).
Also of note, more than 85 percent of the victim sites operated on the Magento CMS. Magento is known to be the top target for Magecart attacks, and has more than 250,000 users worldwide. Magento 1 reached end-of-life last week, with Adobe making a last-ditch effort to urge the 100,000 online stores still running the outdated version to migrate to Magento 2 or face potential targeting from Magecart and other threat groups. Other CMS platforms that were hit by Keeper’s campaign included sites using WordPress (5.5 percent), Shopify (4.2 percent), BigCommerce (2 percent) and PrestaShop (0.5 percent) sites.
These victims may have been “operating on an outdated content management system (CMS), utilizing unpatched add-ons, or having administrators’ credentials compromised through sequel injections,” said researchers.
Changing Tactics
Researchers warned that Keeper appears to be continually updating its tactics and techniques, helping it to skirt detection. For instance, one of the initial attacks launched in April 2017, against retailer dressedinwhite[.]com, utilized public obfuscation methods, which made it simple to decode. Starting in 2018, however, the threat actors began to use custom obfucscation methods, as seen in an attack against casterdepot[.]com, researchers said.
A more recent campaign in 2019 against nomin[.]net also shows a modified script that appears to be much cleaner and more concise with no displayed line breaks, said researchers.
“The Keeper group currently uses this format for its payloads and denotes specific payment card, billing address and additional information fields that it collects,” researchers said.
Going forward, researchers warn that in mid-2020, Magecart attacks have become a daily occurrence for small to medium-sized e-commerce businesses, from food sites to large retailers like Macy’s. More recently, sophisticated hackers like the Lazarus Group have started adding digital payment-card skimming to their repertoire using Magecart code. Researchers predict that in the future, Keeper will continue its attacks.
“Based on this pattern of successful Magecart attacks, Gemini assesses with high confidence that Keeper is likely to continue launching increasingly sophisticated attacks against online merchants across the world,” they said.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.




0 Commentaires