The Chinese APT has been discovered behind a five-year espionage campaign that compromises government servers – and uses that as leverage for other attacks.
After five years under the radar, the Naikon APT group has been unmasked in a long-term espionage campaign against several governments in the Asia-Pacific region.
The Chinese APT group was first uncovered by Kaspersky researchers in 2015, in attacks against top-level government agencies around the South China Sea. After 2015, Naikon seemingly went silent. However, a recently discovered, widespread campaign reveals the group has actually spent the past five years quietly developing their skills and introducing the “Aria-body” backdoor into their arsenal of weapons.
The campaign, which has accelerated in 2019 and the first quarter of 2020, is targeting countries in the APAC region, including Australia, Indonesia, Philippines, Vietnam, Thailand, Myanmar and Brunei, in a quest to gather geo-political intelligence. Specifically targeted are government ministries of foreign affairs, science and technology, and government-owned companies.
“Naikon attempted to attack one of our customers by impersonating a foreign government – that’s when they came back onto our radar after a five-year absence, and we decided to investigate further,” said Lotem Finkelsteen, manager of threat intelligence at Check Point, in a Thursday analysis.
The Campaign
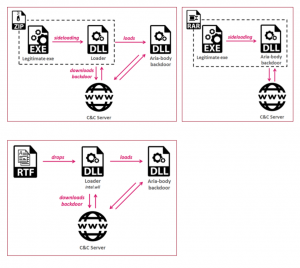
Researchers observed several different infection chains being used to deliver the Aria-body RAT. They first came across the campaign in an email, purporting to be sent from a government embassy in the APAC region, sent to the Australian government. The email contained a document called “The Indians Way.doc.”
This RTF file was weaponized with the RoyalRoad exploit builder. This tool, commonly used by various Chinese threat actors, allows the attacker to create customized documents with embedded objects that typically exploit unspecified vulnerabilities in Equation Editor, a tool for building complex equations in Microsoft Word.
RoyalRoad then drops a loader called “intel.wll” into the victim’s Word startup folder, which ultimately downloads the payload.
Other emails observed utilized other infection methods. For instance, one contained archive files with a legitimate executable, and a malicious DLL, which was loaded in a DLL hijacking technique. Another tactic dropped the payload directly via an executable file, which served as the loader.
Regardless of the infection method, the ultimate downloaded payload is a custom RAT called Aria-body. While Aria-body hasn’t been utilized by the APT group before, it was previously observed as early as 2018, researchers said. After download, the RAT comes with a slew of capabilities, including creating and deleting files, taking screenshots and searching files.
Various modules have also been added to the RAT over the years, including a USB data-gathering module, a keylogger module (added February 2018), a reverse SOCKS proxy module (added February 2018) and a loading extensions module (added December 2019).
Anti-Detection
Ultimately, Aria-body gives the APT group remote access to the infected PC or network, bypassing security measures.
After exploitation, in addition to collecting sensitive data, Naikon would also use the infrastructures and servers of its victims to launch new attacks, which is what researchers believe helped the group evade detection for so long. In one example, for instance, researchers found a server used in attacks belonged to the Philippine Government’s department of science and technology.
“Naikon’s primary method of attack is to infiltrate a government body, then use that body’s contacts, documents and data to launch attacks on others, exploiting the trust and diplomatic relations between departments and governments to increase the chances of its attack succeeding,” said researchers.
Looking ahead, researchers said that Naikon will continue to pose as a significant threat, particularly as it uses new server infrastructure, ever-changing loader variants, in-memory fileless loading and a new backdoor.
“We’ve published this research as a warning and resource for any government entity to better spot Naikon’s or other hacker group’s activities,” said Finkelsteen.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.
Also, don’t miss our latest on-demand webinar from DivvyCloud and Threatpost, A Practical Guide to Securing the Cloud in the Face of Crisis, with critical, advanced takeaways on how to avoid cloud disruption and chaos.



0 Commentaires