
The Kazakh native made headlines last year for hacking McAfee, Symantec and Trend Micro; but the Feds say he’s also behind a widespread backdoor operation spanning six continents.
“Fxmsp,” a notorious hacker who made headlines last year for allegedly stealing and selling source code and customer access from McAfee, Symantec and Trend Micro, has been outed. He’s a Kazakh national named Andrey Turchin, and according to unsealed court documents, he faces hacking charges dating back to 2018.
The documents were unsealed by the Western District of Washington after Fxmsp was profiled and his real name revealed by security firm Group-IB, in an analysis last month that went largely unreported. Seamus Hughes, the deputy director of the Program on Extremism at George Washington University, tweeted out the court documents on Tuesday.
According to the Feds’ allegations, Turchin is a member of a “prolific, financially motivated cybercriminal group composed of foreign actors that hacks the computer networks of a broad array of corporate entities, educational institutions and governments around the world, including the United States, and advertises and sells such unauthorized access to its victims’ protected systems.”
The documents also allege that the group’s tactics are myriad, including brute-force attacks and phishing schemes; the group also used specially designed code to scan the Internet for open Remote Desktop Protocol (RDP) ports.
“Once inside the victim’s system, he moved laterally throughout the network and deployed additional malicious code to locate and steal administrative credentials and establish persistent access,” according to the documents. “The conspirators often modified antivirus software settings to allow malware to continue to run undetected.”
Once the backdoors were established and credentials stolen, the wares went up for sale across various Russian hacking forums, with prices that ranged into the hundreds of thousands of dollars. Last year’s pricing for the security firm data was put up for sale for $300,000, according to a separate report from Advanced Intelligence.
“Prices typically ranged from a couple thousand dollars to, in some cases, over a hundred thousand dollars, depending on the victim and the degree of system access and controls,” the Department of Justice said in a media statement. “Many transactions occurred through use of a broker and escrow, which allowed interested buyers to sample the network access for a limited period to test the quality and reliability of the illicit access.”
Fxmsp even hired a fellow cybercriminal going by “Lampeduza” (a.k.a. Antony Moricone, BigPetya, Fivelife, Nikolay, tor.ter, Andropov or Gromyko) as his sales manager in early 2018.
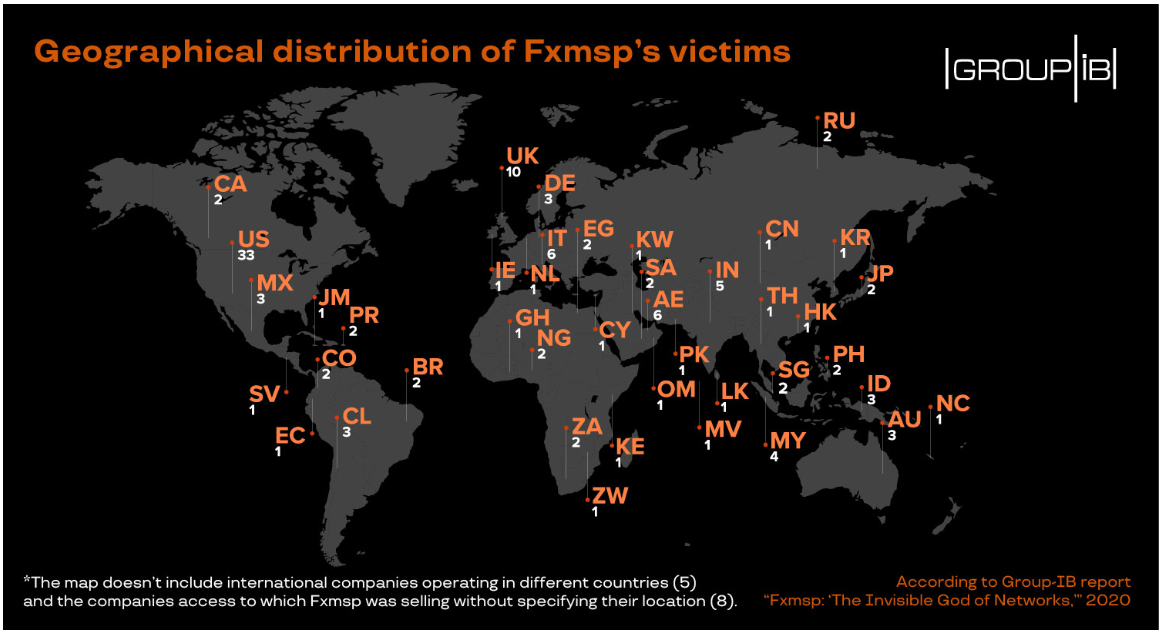
U.S. officials said that overall, the group has made an estimated $1.5 million by stealing information from more than 300 targets across six continents and 44 countries – including 30+ victims in the States.
According to Group IB’s exposé, Lampeduza claimed that the offerings will allow “access to the company’s entire network … You will become THE INVISIBLE GOD OF NETWORKS…”
The firm also detailed Turchin’s tactics: “After gaining access to the target device, Fxmsp usually disables the existing antivirus software and firewall, then creates additional accounts. Next, he uses the Meterpreter payload on servers as a backdoor. Fxmsp himself noted in his posts that, when installing backdoors, he set a long interval for connections with C2 servers: once every 15 days. Once the access is gained, Fxmsp harvests dumps of all the accounts and decrypts them. Finally, he infects the backups by installing backdoors.”
Even if the victim noticed suspicious activity in the system, changing passwords and resetting to backups would be of no avail, since the backdoors were in place and the backups had already been compromised.
“Fxmsp is one of the most prolific sellers of access to corporate networks in the history of the Russian-speaking cybercriminal underground,” Group-IB’s Dmitry Volkov said in a June blog posting. “Despite rather simplistic methods he used, Fxmsp managed to gain access to energy companies, government organizations, and even some Fortune 500 firms.”
The court documents lay out five felony charges against Turchin, going back to 2018 when investigators from the FBI, the U.K.’s National Crime Agency and private security companies uncovered his true identity. These include conspiracy to commit computer hacking, two counts of computer fraud and abuse (hacking), conspiracy to commit wire fraud and access-device fraud.
Turchin is unlikely to be prosecuted anytime soon: Kazakhstan does not have an extradition treaty with the United States, and because Turchin is a Kazakh citizen, the case will likely be prosecuted in that country.
While activity under the handle “Fxmsp” disappeared after the security-firm incidents, Volkov believes the activity could continue, just under a different moniker.
“It is uncertain…whether he is still breaking into company networks and continues to make private offers,” he wrote.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.



0 Commentaires