Various cyber criminal groups and individual hackers are still exploiting a recently patched critical code execution vulnerability in WinRAR, a popular Windows file compression application with 500 million users worldwide.
Why? Because the WinRAR software doesn’t have an auto-update feature, which, unfortunately, leaves millions of its users vulnerable to cyber attacks.
The critical vulnerability (CVE-2018-20250) that was patched late last month by the WinRAR team with the release of WinRAR version 5.70 beta 1 impacts all prior versions of WinRAR released over the past 19 years.
For those unaware, the vulnerability is “Absolute Path Traversal” bug that resides in the old third-party library UNACEV2.DLL of WinRAR and allows attackers to extract a compressed executable file from the ACE archive to one of the Windows Startup folders, where the malicious file would automatically run on the next reboot.
Therefore, to successfully exploit this vulnerability and take full control over the targeted computers, all an attacker needs to do is just convincing users into opening a maliciously-crafted compressed archive file using WinRAR.
Immediately after the details and proof-of-concept (PoC) exploit code went public, malicious attackers started exploiting the vulnerability in a malspam email campaign to install malware on users’ computers running the vulnerable version of the software.
Now, security researchers from McAfee reported that they identified more than “100 unique exploits and counting” in the first week since the vulnerability was publicly disclosed, with most of the initial targets residing in the United States.
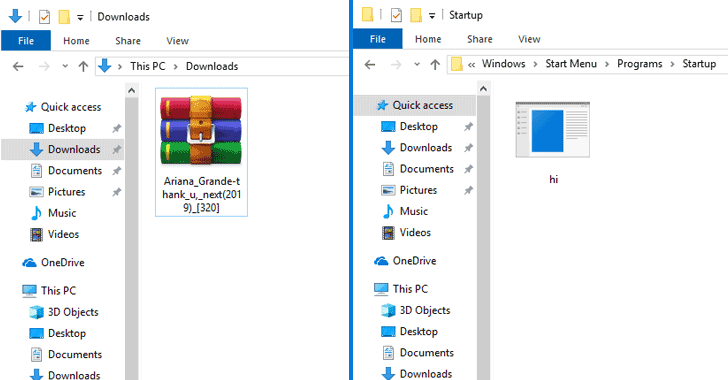
One recent campaign spotted by the researchers piggybacks on a bootlegged copy of an Ariana Grande’s hit album, which is currently being detected as malware by only 11 security products, whereas 53 antivirus products fail to alert their users at the time of writing.
The malicious RAR file (Ariana_Grande-thank_u,_next(2019)_[320].rar) detected by McAfee extracts a list of harmless MP3 files to the victim’s download folder but also drops a malicious EXE file to the startup folder, which has been designed to infect the targeted computer with malware.
“When a vulnerable version of WinRAR is used to extract the contents of this archive, a malicious payload is created in the Startup folder behind the scenes,” the researchers explain.
“User Access Control (UAC) is bypassed, so no alert is displayed to the user. The next time the system restarts, the malware is run.”
Unfortunately, such campaigns are still ongoing, and the best way to protect yourself from such attacks is to update your system by installing the latest version of the WinRAR software as soon as possible and avoid opening files received from unknown sources.



0 Commentaires