Novel hack allows an attacker to create a mouse-over in a PowerPoint file that triggers the installation of malware.
A researcher is sounding the alarm over what he believes could be a novel attack vector which allows a hacker to manipulate a PowerPoint file to download and begin the installation of malware, simply by hovering over a hypertext link.
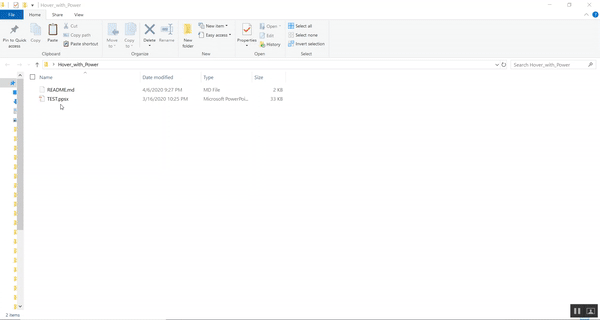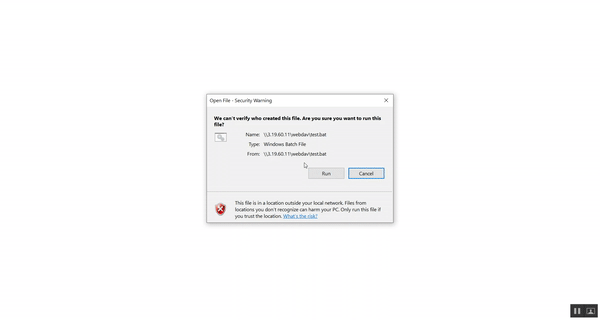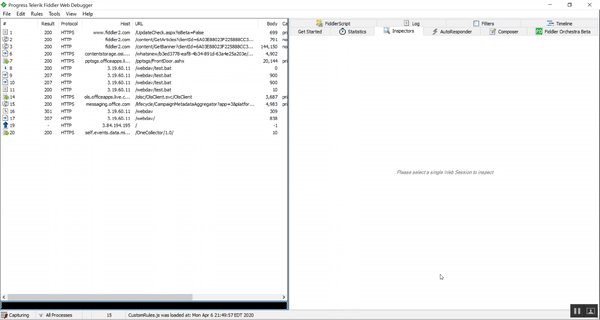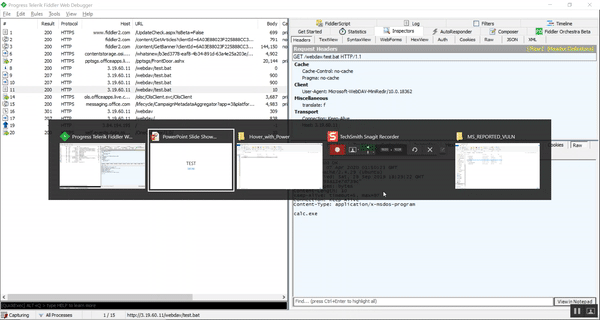
The technique does require a victim to accept one pop-up dialogue box to run or install a program. For those reasons, Microsoft does not consider this a vulnerability. Mandar Satam, independent security researcher, disagrees.
“The attack is able to bypass the PowerPoint’s restriction of not being able to add a remote file to the HyperLink action, which if we try to add using the GUI, we can’t,” Satam told Threatpost. He added that the dialogue box text containing the filename can be manipulated to show anything, including “Windows Update.bat” or “Loading.. Please Wait.exe.” Satam, who created a proof-of-concept attack using the technique, said the “weakness” is in PowerPoint’s Open XML Slide Show files, called PPSX. These type of PowerPoint files are designed for presentation playback only, and can’t be edited.
Satam, who created a proof-of-concept attack using the technique, said the “weakness” is in PowerPoint’s Open XML Slide Show files, called PPSX. These type of PowerPoint files are designed for presentation playback only, and can’t be edited.
“In PowerPoint it is possible to set an action on a mouse-over,” he said. In his PoC attack, dubbed “Hover with Power,” Satam bypasses previous PowerPoint restrictions implemented by Microsoft in 2017, to prevent malicious links in PowerPoint from installing local executable programs just by hovering over a hypertext link.
“Since that vulnerability was patched, this one is an extension to it where instead of using ‘Run Program’ action we use ‘HyperLink To’ action and set it to an ‘Other file’,” the researcher wrote in a technical walkthrough of his research.
By swapping “Run Program” for “HyperLink To,” the PoC runs the executable from a remote server “an attacker-controlled web server with Web Distributed Server (WebDAV) extensions.” This type of server allows remote content editing and reading.
“Due to the way SMB connections work in Windows 10, SMB connections over the internet are possible even if SMB ports (445/139) are closed if a webserver supporting WebDAV extension is hosted by an attacker,” the researcher wrote.
The Windows Server Message Block (SMB) protocol provides file sharing, network browsing, printing services, and inter-process communication over a network. In the context of Satam’s PoC it circumvents a reliance of a noisy HTTPS request that would likely alert an end user to malicious activity.
“If an HTTP/HTTPS URL is linked with the (PowerPoint) hyperlink action, then the OS would download the file using a browser on the system at which point Windows Defender/Smartscreen would kick in, indicating that it is an untrusted file; and even if we hit ‘Run’, it will quarantine the file,” the researcher wrote.
Because the Hover with Power attack only triggers one pop-up dialogue box – which can be manipulated by the attacker – the researcher views this as a vulnerability. However, when he contacted the Microsoft Security Response Center (MSRC), he was told on April 2 that his inquiry would be “closed” because the attack requires an element of social engineering.
“Unfortunately, your report appears to rely on social engineering to accomplish, which does not meet the bar for security servicing… As such, this thread is being closed and no longer monitored,” MSRC wrote back to the researcher.
A Threatpost inquiry to Microsoft echoed the same. “For this social-engineering technique to be successful, the user must first take action to dismiss the security warning. We encourage our customers to practice good computing habits, including exercising caution when clicking on links to web pages, opening unknown files or accepting file transfers,” a Microsoft spokesperson wrote in a statement.
Below is an animation of the “Hover with Power” PoC in action:
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.


0 Commentaires