As mentioned in previous articles, Securonix, has devoted an entire taskforce to outlining key threats that are appearing under the guise of COVID-19 themed domain names or emails. The threat research team has been observing malicious threat actors attempting to exploit an increasing number of the associated cyberattack vectors such as:
- Ransomware using weaponized COVID-19/coronavirus-related documents disrupting critical healthcare and other businesses’ operations;
- Custom COVID-19 themed phishing attacks involving malicious documents to steal remote workforce credentials and infiltrate various organizations;
- Malware using fake live coronavirus maps/tailored monitoring applications for malicious purposes, DNS hijackers changing important records;
- Malicious and trojaned applications/.apks related to coronavirus exploiting remote workforce’s BYOD/Android devices;
- Attacks exploiting remote access/VPN servers taking advantage of the worldwide increase in the number of remote users.
Securonix’s Threat Research Team has been actively investigating and closely monitoring the cyberattacks and the current shift towards a remote workforce to help businesses improve the security of the remote users to increase the chances of detecting both current and future critical cyberattacks early in the changing environment. This is in order to minimise the likelihood of disruptions that will affect core business operations.
In order to help businesses, Securonix has compiled a series of relevant details and recommendations to help enterprises manage the monitoring of a remote workforce, including some details about the cyberattacks observed and examples of threats in the wild in order to help security operations/SOC, IT operations, Insider threat teams, and Human resources.
Most of the ransomware appearing seems to be a variant of the SNSLocker, propagated through a malicious COVID-19 situation report (sitrep) e-mail:
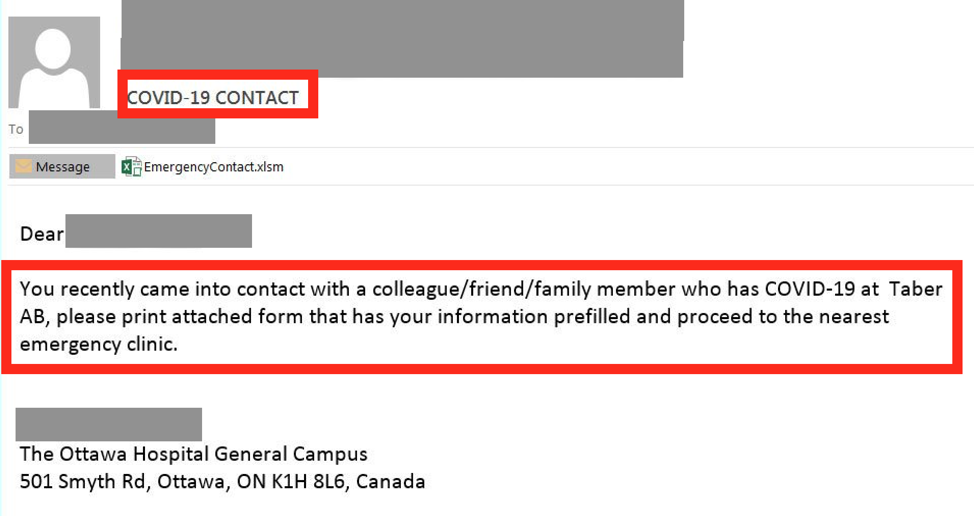
Figure 1: A fake COVID-19 Infection Phishing E-mail
Once a user opens the document, this is immediately followed by the sensitive data being encrypted by the ransomware:

Figure 2: Covid19/Coronavirus-themed Weaponized Excel Document Ransomware
We have also seen a rise in COVID-19 related credential stealing. These are often pushed through various e-mails, such as fake COVID-19 infection notification e-mail. If opened, the implant then downloads a second stage malware with multiple variants appearing within some of the logs observed shown in Figure 3. Once these have been installed on your device, they have the potential to perform malicious actions such as Stealing web browser cookies, enumerate system information and shares; Stealing cryptocurrency wallets; and Exfiltrating stolen information.
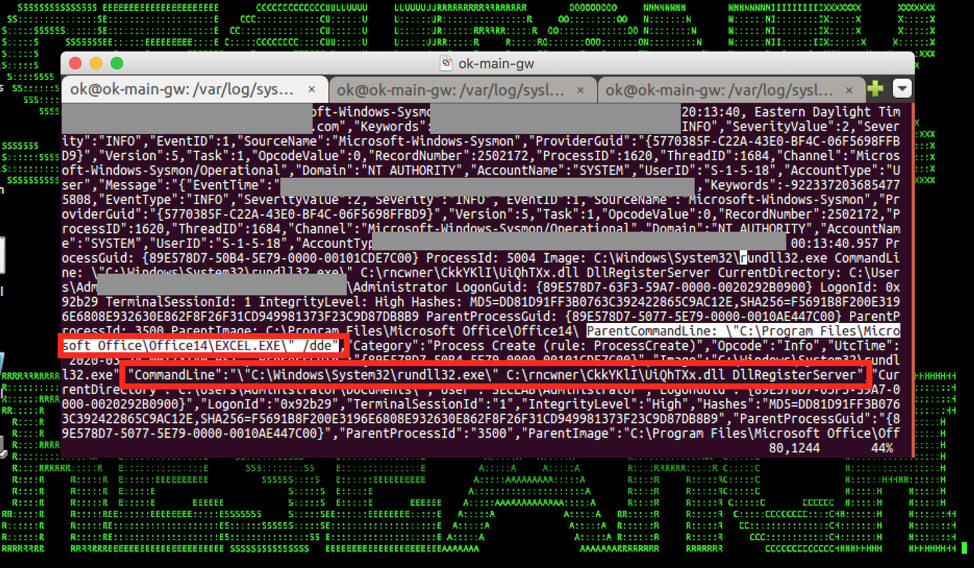
Figure 3: Fake COVID-19 Infection Phishing E-mail – Initial weaponised doc exploit loading a malicious DLL
There are several recommended log/data sources to help security teams relevant cyberattack variants as part of remote workforce/WFH monitoring. Firstly, Securonix recommends using VPN server logs. In order to enable the proper visibility, enterprises should consider reviewing VPN policies to ensure that split-tunneling in order to achieve the highest level of visibility possible. Secondly, cloud application/Software-as-a-Service (SaaS) logs should be used by remote workforce users. Thirdly, single-sign-on (SSO) and 2FA/MFA logs should be used to limit unauthorised access. Finally, EDR/Remote workstation logs, Email gateway logs, CASB, and other logs can be used to maintain security.
What are some of the priority use cases recommended?
Some of the most important use cases recommended by Securonix include:
- Unusual severity event for your VPN server device; Account authentication from a rare geolocation;
- VPN connection from an anonymous proxy;
- Connection to a rare domain for a peer group followed by an executable download;
- Emails from typosquatted domain;
- Abnormal number of emails or data sent to a rare external recipient;
- Unusual VPN session length or data access
- Unusual sensitive data access increase for a user
This abnormal time is difficult for security teams and individuals; however, this time will come to an end. In the meantime, we must all work together to ensure that the most sensitive data is protected at all times. This is an ongoing task; however, it is one that must be completed if we are to win the persistent battle against cybercriminals.



0 Commentaires