Hundreds of thousands of malware files are disguised as well-known social conferencing and collaboration apps.
Popular conferencing apps have become a major cybercrime lure during the COVID-19 work-from-home era – and Skype is the undisputed leader when it comes to being impersonated by malicious downloads, researchers have found.
An April analysis from Kaspersky uncovered a total of 120,000 suspicious malware and adware packages in the wild masquerading as versions of the video calling app.
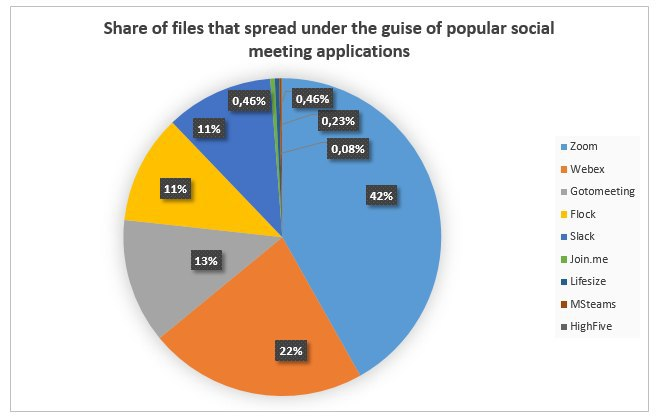
It should be said that Skype isn’t alone in being targeted: The research found that among a total of 1,300 suspicious files not using the Skype name, 42 percent were disguised as Zoom, followed by WebEx (22 percent), GoToMeeting (13 percent), Flock (11 percent) and Slack (11 percent).
“With the rise of social distancing, Kaspersky experts investigated the threat landscape for social meeting applications to make sure users are safe and their communication experience is enjoyable,” the firm said in an emailed analysis. “Social meeting applications currently provide easy ways for people to connect via video, audio or text when no other means of communication are available. However, cyber-fraudsters do not hesitate to use this fact and try to distribute various cyberthreats under the guise of popular apps.”
Some of the files found turned out to be simply knockoff versions of the real thing, but among the actual threats detected, a few malwares and file types came to the fore, including two adware families: DealPly and DownloadSponsor.
“Both families are installers that show ads or download adware modules,” according to the analysis. “Such software typically appears on users’ devices once they are downloaded from unofficial marketplaces.”
There were also some malware threats disguised as .LNK files – shortcuts to applications – that Kaspersky detected as Exploit.Win32.CVE-2010-2568. This is “an old, yet still widespread malicious code that allows attackers to infect the target with additional malware,” according to the firm. The old, patched vulnerability it uses is a Windows Shell that is not properly handled during icon displays in Windows Explorer, which allows arbitrary code execution via specially crafted .LNK or .PIF shortcut files. It affects Windows XP, Vista and Windows 7, mostly.
Trojans were also a popular malware type found in the fake apps, especially Skype, the firm found.
“In the current landscape, when most of us are working from home, it is extremely important to make sure that what we use as a tool for online social meeting is downloaded from a legitimate source, set up properly and doesn’t have severe unpatched vulnerabilities,” said Denis Parinov, security expert at Kaspersky, via email.
Do you suffer from Password Fatigue? On Wednesday April 8 at 2 p.m. ET join Duo Security and Threatpost as we explore a passwordless future. This FREE webinar maps out a future where modern authentication standards like WebAuthn significantly reduce a dependency on passwords. We’ll also explore how teaming with Microsoft can reduced reliance on passwords. Please register here and dare to ask, “Are passwords overrated?” in this sponsored webinar.




0 Commentaires