Threat actors are spreading the tricky trojan through fake messages in another opportunistic COVID-19-related campaign, said IBM X-Force.
Threat actors are using people’s interest in the Department of Labor’s Family and Medical Leave Act (FMLA) to spread what appears to be the TrickBot trojan in a new spam campaign that security researchers discovered recently.
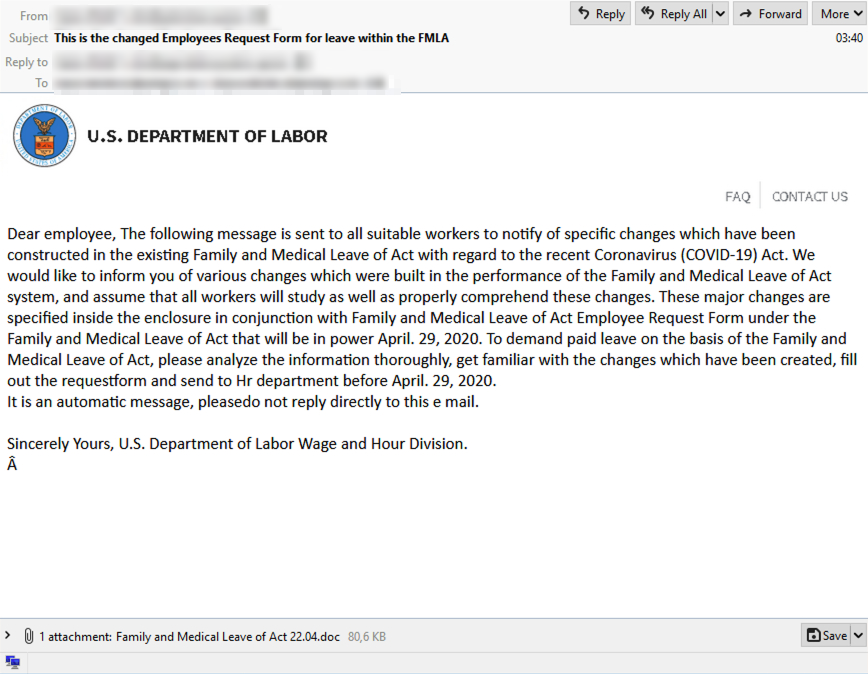
Recent analysis from spam honeypots set by IBM X-Force discovered actors targeting email recipients with fake messages that claim to be from the department to inform people of changes to the FMLA, which gives employees the right to family-leave medical benefits, according to a post by IBM security analyst Ashkan Via. Instead, the emails include malicious attachments aimed at installing what researchers believe is the TrickBot malware, they said.
TrickBot is a well-known and sophisticated banking Trojan first developed in 2016 as a banking malware that has a history of transforming itself and adding new features to evade detection. It’s developed over the years into a full-fledged, module-based crimeware solution typically aimed at attacking corporations, though the latest campaign seems to deviate from that target audience.
“Users infected with the TrickBot Trojan will see their device become part of a botnet that can allow attackers to gain complete control of the device,” Via, along with IBM X-Force co-authors David Bryant and Limor Kessem, wrote in the post. “Typical consequences of TrickBot infections are bank account takeover, high-value wire fraud, and possibly ransomware attacks targeting organizational networks.
The threat actors behind the latest campaign also are some of the myriad taking advantage of the COVID-19 pandemic and resulting economic crisis, which has many in the United States seeking financial support through federal government programs.
One curious thing about the research is that the samples observed by the IBM X-Force failed to actually download their intended payload, which researchers acknowledge made it difficult to know for sure if the campaign’s malware is indeed TrickBot.
However, researchers said the new campaign follows “similar patterns” found previously used by TrickBot, such as the “Macro on Close” function followed by the DocuSign theme.
“Another link to TrickBot is an IP address, 198.72.111.141, also previously linked with hosting TrickBot campaigns,” researchers wrote. However, “it is possible that malware is being distributed by the same parties and the final payload is possibly different, but TrickBot mostly uses the same distribution channels compared to more commercialized malware.”
The first sample IBM X-Force researchers observed was an email that contained a Microsoft Office Themes File called “US-DoL.eml”. That file contained three attachments: us-logo.png, faq.png and Family and Medical Leave of Act 22.04.doc, with the final document file being the malicious component, they said.
“Once opened, the document asks the recipient to enable macros (ThisDocument.cls), from which, upon closing the file, malicious scripts will be launched to fetch the malware from the attacker’s designated domain,” researchers wrote.
The macro begins its dirty work by creating a local directory, C:Test, and drops a batch file, terop.bat, to that location. It then executes that file: C:Testterop.bat, using various other files along the infection chain, according to the post.
IBM X-Force researchers attributed the campaign to the “endless amounts of spam and attacks targeting users across the globe” due to the COVID-19 pandemic. Indeed, myriad new email-based malware campaigns have surfaced since the pandemic and ensuing global lockdowns began in earnest in mid-March, with researchers from Forcepoint clocking 1.5 malicious emails per day at the height of the activity.
“The current spam is likely an early warning to those expecting to take advantage of the FMLA during the pandemic to be on the lookout for malicious campaigns,” Via and his co-authors wrote. “TrickBot spam varies frequently depending on those distributing it, and the issues we detected in the macro scripts are likely to be fixed and relaunched in further spamming activity.”
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.
Also, don’t miss our latest on-demand webinar from DivvyCloud and Threatpost, A Practical Guide to Securing the Cloud in the Face of Crisis, with critical, advanced takeaways on how to avoid cloud disruption and chaos.


0 Commentaires