DDG might be the world’s first P2P-based cryptomining botnet.
The coin-mining botnet known as DDG has seen a flurry of activity since the beginning of the year, releasing 16 different updates over the course of the past three months. Most notably, its operators have adopted a proprietary peer-to-peer (P2P) mechanism that has turned the DDG into a highly sophisticated, “seemingly unstoppable” threat, according to researchers.
DDG was first flagged in January of 2018 by Netlab 360, which went on to sinkhole the malicious operations. The firm was able to do so because DDG used static IP and DNS links for its command-and-control (C2) communications, which were easily subverted. At that point, DDG had only infected 4,391 public-facing servers to mine the Monero cryptocurrency, according to the firm, and didn’t seem like a particularly notable threat.
A year later however, DDG had come roaring back, with a total of 5,695 devices enslaved as bots in January 2019. Netlab 360 said that its analysis at the time showed that the operators had added a Memberlist-based P2P mechanism, mainly used for back-up C2 communications.
Since then, the botnet has been under active and constant development, Netlab 360 explained, with most iterations representing only incremental changes. Then, in February of this year, Netlab 360 researchers saw DDG making what the firm called a “major change” – developing its own P2P protocol.
Proprietary P2P
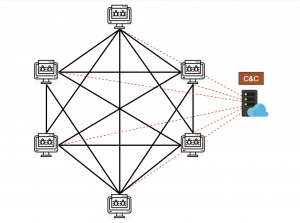
In its latest version, the DDG botnet still uses IP or DNS for static C2 communications, but its new P2P network acts as “a fall-back [failsafe] that even if the C2 is taken down, the infected devices are still going to keep going and perform the mining tasks,” analysts said in a blog on Wednesday (translated for Threatpost from Chinese via Google Translate).
Using the protocol, the operators have essentially built a redundant network where each node (a.k.a. “peer”) communicates with 200 other nodes. These nodes can share the latest C2 addresses, a list of other nodes to communicate with, malicious task instructions (including directions to delete competitor miners) and configuration information amongst themselves, across many paths. Also, they can spread malicious components between themselves as needed.
“Peers have unique ping-pong mechanism,” according to the researchers. “Peers can share their own C2 and peers list data; the slave config and jobs config data can be propagated between peers; [and] peers can spread other payloads or components, such as malicious mining programs, [or] compiled Busybox binaries.”
The unique architecture also sports a proxy feature that can be used between peers, according to the analysis.
“When a peer requests to download the miner program or a Busybox program, if the DDG finds that there is no corresponding file in its working directory, it will use itself as a proxy and randomly send the request for the corresponding file to other peers that it has successfully connected to,” the firm explained. “If the download is successful, it will be returned to the peer requesting to download the file.”
All of this means that should C2 communications be cut off, the nodes can continue their operations within their self-contained network. In all, it’s a highly evolved and sophisticated architecture, according to Netlab 360.
“After more than two years of development, DDG has evolved from a simple mining trojan, to a simple P2P network using a third-party protocol framework, to using a self-developed P2P protocol,” researchers concluded. “It has evolved into a complex P2P botnet – and maybe this is the first P2P mining botnet in existence.”
There have, however, been other types of peer-to-peer (P2) botnets, such as Roboto, Hajime and Joanap, which focus on carrying out distributed denial of service attacks and the like. The few that have been observed in the wild operate without a C2 server at all, making it trickier for researchers or authorities to target them as there’s no centralized domains or servers to track.
Growing Slowly but Steadily
In tracking the specific protocol, the researchers were able to identify 900 active IP nodes in the P2P network, each representing multiple infected devices or bots.
“According to statistics provided by our partners, there are 17,590 active bots in mainland China,” according to the firm. “According to our tracking data, the number of bots in mainland China accounts for about 86 percent of the total, from which in turn it can be inferred that DDG currently has about 20,000 bots worldwide.”
It’s not huge by botnet standards (the infamous Necurs had 9 million bots at the time of its takedown), but DDG is likely highly effective, the firm said. “It is probably safe to bet this botnet is making very good profits, the author probably is pretty happy with the already compromised devices he’s got, and he wants to stay low-profile, and is in no rush to expand his bot army.”
Interestingly, DDG has a niche attack vector, choosing to exclusively target servers on corporate intranets –specifically, it targets servers that have weak SSH passwords for one single user name root. It has a hardcoded list of 17,907 passwords that it tries against its targets, Netlab 360 researchers said.
“[We’re hoping] more security researchers can take a good look at it and hopefully slow down the seemingly unstoppable DDG botnet,” they added.
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.



0 Commentaires