More than 150,000 emails spreading the Hupigon RAT that use adult dating as a lure have been uncovered, with almost half being sent to U.S. university and college email addresses.
Several U.S. universities have been targeted in a widespread spear-phishing attack that uses adult dating as a lure. In reality, the emails spread the Hupigon remote access trojan (RAT), known to be leveraged by state-sponsored threat actors.
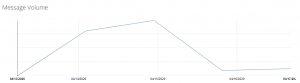
Researchers from Proofpoint warned that the ongoing spear-phishing campaign has sent more than 150,000 messages to 60+ different industries – with almost half of the malicious emails focused on the education space, including several unnamed colleges and universities. The bulk of the messages (80,000 emails) were mostly sent between April 14 and 15.
The emails use an adult dating lure, sending the victim two pictures of women and requesting the recipient to choose one to connect with by clicking the link under the picture. After the recipient clicks the link, an executable download begins (the file is named “sex_Live1.5.0.1099.exe”) that then installs the Hupigon RAT onto the system.
The Hupigon RAT, which has been active since at least 2006, has various data exfiltration features and capabilities and has been previously utilized by advanced persistent threat (APT) actors. It gives attackers rootkit functionality, webcam monitoring capabilities, and the ability to log keystrokes and steal passwords.
 “In this case, cybercriminals repurposed a nearly 15-year-old attack tool leveraged by state-sponsored threat actors, among others. We believe this campaign is crimeware-motivated,” said Proofpoint researchers, in an analysis last week. “Proofpoint associates Hupigon with historic APT campaigns based on the language of the builder, open-source breach reporting and multiple reports of similar APT actor behaviors between 2010 and 2012.”
“In this case, cybercriminals repurposed a nearly 15-year-old attack tool leveraged by state-sponsored threat actors, among others. We believe this campaign is crimeware-motivated,” said Proofpoint researchers, in an analysis last week. “Proofpoint associates Hupigon with historic APT campaigns based on the language of the builder, open-source breach reporting and multiple reports of similar APT actor behaviors between 2010 and 2012.”
Other details remain scant about the campaign, other than the fact that the payload makes a DNS request to eth[.]ceo located at 142.54.162[.]66 for the initial command-and-control (C2) communication. Researchers also noted that the domain used for delivery, down.gogominer[.]com, is hosted on the same address space as the C2, 142.54.162[.]67.
Threatpost has reached out to Proofpoint for more information about the campaign, including any evidence of whether APT groups are behind this particular attack.
The attacks come as universities and colleges face unprecedented remote-work security issues, after having to send students home and set up courses online due to the coronavirus pandemic.
Previously uncovered malware campaigns have targeted the healthcare and education industries, including one targeting a Canadian medical research university. Other schools have been hit by Zoom-bombing attacks, where attackers hijack online classes using the Zoom platform to spew hateful messages or videos.
Universities were targeted even before the ongoing pandemic forced them to move coursework online: In September 2019, a massive campaign was uncovered involving at least 20 new phishing domains, targeting more than 60 universities in Australia, Canada, Hong Kong, Switzerland, the United Kingdom and the United States. The campaign, bent on lifting credentials from students heading back to school, was associated with a group of Iranian cyberattackers collectively known as Cobalt Dickens or Silent Librarian.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.




0 Commentaires