
A new Android trojan targets banking customers with overlay attacks to steal their bank credentials and ultimately take over their accounts.
A recently uncovered banking trojan aims to steal Android victims’ online banking credentials and take over their bank accounts, using “elaborate” overlay attack capabilities.
The malware, dubbed “Banker.BR” by researchers with IBM X-Force, was spotted in messages targeting users in countries that speak Spanish or Portuguese (including Spain, Portugal, Brazil and other parts of Latin America). Researchers said the malware is under continual development, and they warned of extended overlay capabilities and code enhancements in the coming months.
“According to our analysis, Banker.BR’s code is entirely new and does not rely on previously leaked code or existing mobile malware,” said Ben Wagner and Limor Kessem, IBM X-Force researchers, in a Tuesday analysis. “While our team has seen earlier versions of this trojan, which only featured a basic SMS stealer, [the latest version has a] new, and more elaborate, feature of the overlay malware capability — a tactic common to most Android banking malware.”
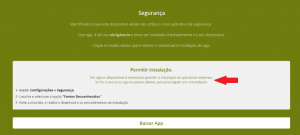
The malware is spread via messages that lead users to a malicious domain controlled by the attackers. The domain instructs victims to download the most recent version of a purported “security app” required for mobile banking. If victims click the update button, they unwittingly launch the malware download from a legitimate file-sharing platform.
Limor Kessem, executive security advisor at IBM Security, told Threatpost that the particular file sharing platform has not been disclosed – but “its identity does not necessarily play an important role since criminals constantly change it to evade detection and blocking,” he said.
Banker.BR is programmed in the B4X programming language, which is a modern version of Visual Basic that’s part of a suite of rapid integrated development environments (IDEs), used to create Android and iOS applications. B4X is not often used for malware, which are instead usually implemented in the Java/Kotlin programming languages (part of the Android studio development essentials platform).
After being installed on the victim’s device, the malware scoops up device information – including phone number, International Mobile Equipment Identity (IMEI), International Mobile Subscriber Identity (IMSI) and SIM serial number – and sends it the command and control (C2) server, which is a domain address hardcoded into the malware.
Similar to other overlay malware strains, Banker.BR abuses the Accessibility service on phones in order to grant itself permissions on the phone without the victim’s knowledge (Android says that accessibility services are typically used to assist users with disabilities in using Android devices and apps). These permissions give the malware to access contacts, camera, SMS messages and more.
“Abusing the Accessibility service on the device, a relatively common way for Android malware apps to keep tabs on which app is running in the foreground, [Banker.BR] waits for a match with the goal of launching overlay screens at the right time and context to fool the user into tapping their credentials into the overlay,” said researchers.
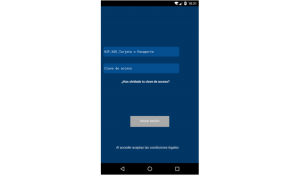
Once the victim goes to a banking domain, the malware then deploys an overlay screen, which typically features the bank’s logo and asks for the user’s sign-in credentials. The victim enters these credentials, unwittingly giving them to the attacker — who can now access the victim’s bank account and launch fraudulent transfers. The malware can also exfiltrate victims’ SMS messages, which allows it to grab any potential two-factor authentication (2FA) codes sent to the user by the bank, if need be.
Banker.BR contains some blips that show it’s clearly still under early development. For instance, the malware isn’t obfuscated, making it easier to reverse-engineer, researchers said. And the trojan does not verify whether it is running in a virtualized environment (or if it is being debugged) before it installs on a device.
Also, unlike similar overlay malware, Banker.BR’s overlay screens are embedded into the malware and not retrieved from the attacker’s C2 server in real time. Researchers said this is “a less agile method that does not allow for on-the-fly updates to fake screens, but rather requires a malware update to deliver changes. It also exposes all the available screens to outsiders analyzing the malware.”
Despite these drawbacks, researchers said it’s clear that Banker.BR is becoming more sophisticated. For instance, early on, the malware was only able to steal SMS messages – but it has since evolved to add the overlay attack capabilities. Researchers warned that there could be upcoming developments, such as new overlay screens being added for additional targeted banks.
“We do think Banker.BR is a work in progress and that we may see advancements in the coming months, however at this time we don’t know the precise skill level and abilities of the developers,” Kessem told Threatpost. “Currently the malware is not considered to be very sophisticated, but it’s certainly effective and that level of sophistication can change over time – as is often the case with malware.”
He added, “so far this year we are seeing more attacks on banks in Latin America, so it’s possible that Banker.BR serves as an indication that more cybercrime operators are moving malware from Latin America to Europe in order to take advantage of using tools in the same language without needing to invest in their own. Of course, they still need a localized mule network and resources, like a spamming service and local servers, to operate in a different geography.”
Banker.BR is only the most recent overlay malware to be discovered targeting Portuguese- and Spanish-speaking countries. Earlier in April, researchers warned of a remote overlay malware attack that leveraged a fake Chrome browser plugin to target the accounts of banking customers in Spain.
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.



0 Commentaires