The malware is back in targeted attacks against Brazilian banking customers, this time using a new technique that involves mobile app authorization.
The CamuBot malware, known for targeting Brazilian bank customers, has returned in a slew of recent offensives. The latest wave of attacks are highly personalized and, unlike previous campaigns, target victims’ mobile banking apps as an extra step to evade detection when making fraudulent transfers.
Researchers said they’ve observed the CamuBot malware being distributed in two highly targeted campaigns over the past six months, including one from August to September, and then another from October to November. Now, the onslaught is continuing into 2020, they said. The victims in these campaigns are small business account holders, in charge of companies’ accounts with large banks in Brazil, researchers said.
“Some observations from the campaigns are that the adversary operating CamuBot handpicks potential victims and remains as targeted as possible, likely to keep the attack’s [tactics, techniques and procedures] TTPs on low profile and their team from attracting the attention of local law enforcement,” said IBM X-Force researchers Chen Nahman and Limor Kessem, in an analysis this week.
The highly targeted attacks begin in a similar fashion to an August 2018 campaign, where CamuBot was first spotted. The bad actors begin by conducting extensive research on victim organizations, including making several phone calls to to map out the hierarchy of the company.
Then, posing as bank employees, attackers “groom” the account holders to build trust via phone and email conversations, before eventually asking them to perform various actions in their account, researchers said.
After this period of extended social engineering, attackers eventually call the victims and instruct them to browse to an infected webpage that is hosting the CamuBot trojan. The victims are instructed to enter their banking login credentials into the fake page and download a supposed security application (which in reality is CamuBot). After victims unknowingly download and run CamuBot on their devices, the attacker gains remote-access capabilities to their computers.
New Tactic
While in the previous 2018 campaign, attackers would at that point utilize the victims’ credentials to log into their accounts and make fraudulent transactions, recent campaigns take the attack a step further.
“What stood out to us in more recent activity… is the fact that the attackers do not always take over the account by connecting to the victim’s infected desktop device as they did before,” said the researchers. “Rather, we have been seeing that business accounts are being accessed through the bank’s mobile application.”
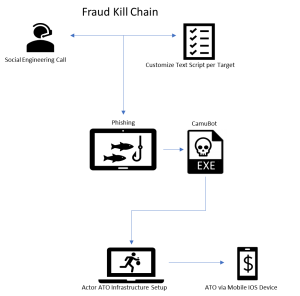 Specifically, after CamuBot infects the victim’s computers, victims are instructed by the attackers over the phone to authorize access to a mobile device app by providing their phone numbers.
Specifically, after CamuBot infects the victim’s computers, victims are instructed by the attackers over the phone to authorize access to a mobile device app by providing their phone numbers.
While attackers already have the online banking credentials, “the attacker in this case wants the victim to authorize activity from the app on the mobile device,” researchers told Threatpost. “Victims are being asked to enable that through the desktop website.”
With this access now authorized by the victim, attackers can then log into the mobile app, using the victims’ stolen credentials, and change the mobile number connected to it to one that they control. Researchers said the likely motive behind this approach is to potentially to have stronger control over any alerts or second-factor token codes sent from the bank.
While attackers already have access to victims’ compromised desktops, “the most likely scenario here is that the attacker is hoping to preserve their access and be able to monitor the account over time until they can plan for a large fraudulent transfer,” they said. “By having the account coupled with a phone number they have access to two-factor authentication (2FA), or verification calls from the bank will end up reaching the criminal and possibly enable them to complete the fraudulent operation.”
In other cases, the attackers used the victim’s actual phone numbers and likely performed a SIM swap (a form of fraud that allows crooks to bypass SMS-based 2FA and crack online banking or other high-value accounts) to defraud the account later down the line, researchers said.
Rise of CamuBot
Researchers said that the tactics of CamuBot are in line with TTPs used by organized cybercrime groups such as TrickBot, IcedID and Ursnif, each of which focuses on business banking and blends social engineering with malware-assisted account and device takeover.
This is different from other popular malware strains in Brazil that utilize more traditional tactics, like remote overlay trojans, to facilitate device takeover and consumer account fraud.
“Unlike most malware we encounter in the Brazilian financial threat arena, CamuBot differs by using a unique code base,” said researchers. “It also stands out in its operators’ brazen way of interacting with potential victims, and instead of concealing the malware, it poses as a security application that banks supposedly require they install.”
Researchers warned that this trend will strengthen in 2020, with more targeted attacks seen in the region and likely additional CamuBot campaigns spotted in the months to come.




0 Commentaires