Thanks to the coronavirus pandemic, the role of the Internet in our lives has undergone changes, including irreversible ones. Some of these changes are definitely for the better, some are not very good, but almost all of them in some way affect digital security issues.
We decided to take a closer look at the changes around us through the prism of information security, starting with the video game industry.
Key findings:
- The daily number of blocked attempts to visit malicious gaming-related websites, or browse to such sites from gaming-related websites (or forums), increased by 54% in Aprilcompared to January of this year. In May, we saw a downward trend in this indicator: -18% compared to April.
- The number of blocked attempts to visit phishing sites that exploit online gaming topics has increased. In particular, the number of notifications from fake Steam gaming platform sites increased by 40% from February to April.
- Attackers use Minecraft, Counter-Strike: Global Offensive and The Witcher 3: Wild Hunt most often.
- The users most targeted by such attacks are from Vietnam (7.9%), Algeria (6.6%), Korea (6.2%), Hungary (6.2%) and Romania (6%)
I play until the boss sees
Figures from various sources show that the pandemic has led to a sharp increase in player activity. In March, according to gamesindustry.biz, sales of games, both computer and console, increased significantly.
Growth in game sales in the week of March 16-22. Source: gamesindustry.biz (download)
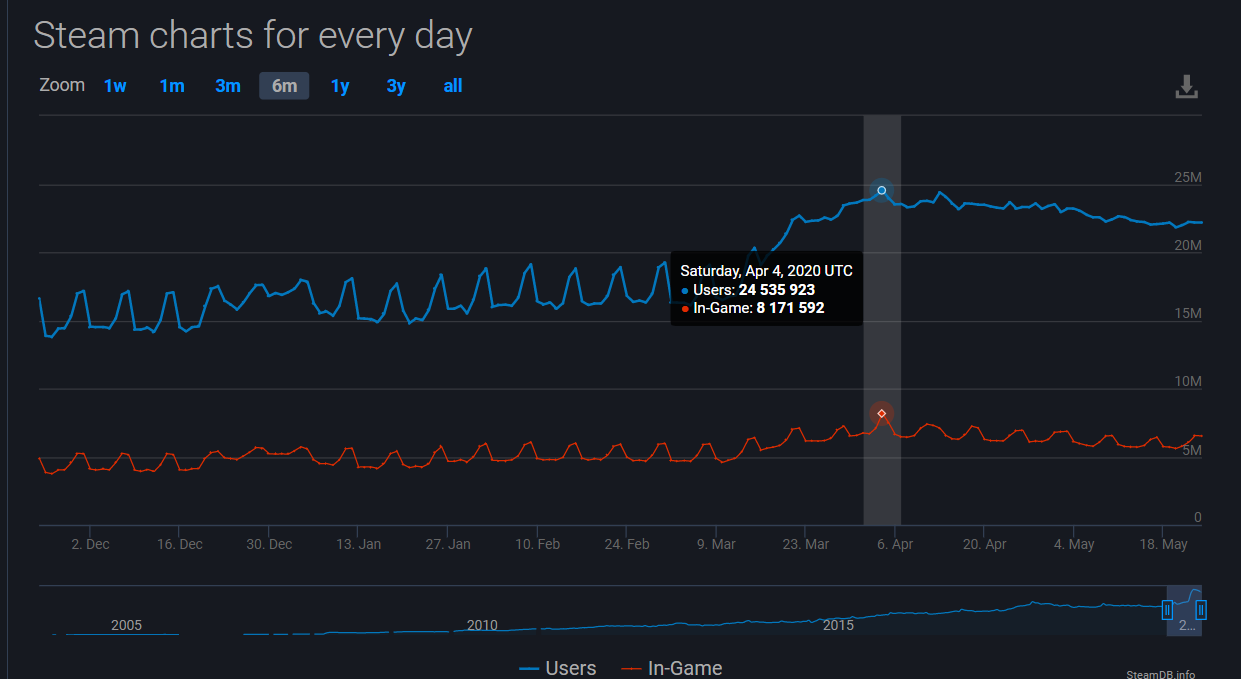
In April, the number of downloads, as well as the number of simultaneous online players, of Steam reached record levels. The Steam user activity graph (both in-game and just installing the client) (Steam Database) shows the peak of activity on April 4. After that, activity started to reduce, but only slowly. Moreover, the activity graphs of the players are noticeably different from the usual ones – periods of inactivity are less pronounced than in ordinary pre-quarantine days, and the peaks last longer.
The number of Steam users per day. Source: steamdb.info
All these stats are totally understandable. First, people have more free time for games. Statistics collected by Nielsen Games as part of their regular survey of gamers confirms this thesis:
The increase in the amount of time spent playing video games by players in different countries. Source: Hollywood Reporter (download)
Second, apparently not all people who wanted to spend time playing video games had a computer at home that would let them do it. That’s what you can figure out checking out the hardware statistics displayed on the Steam site.
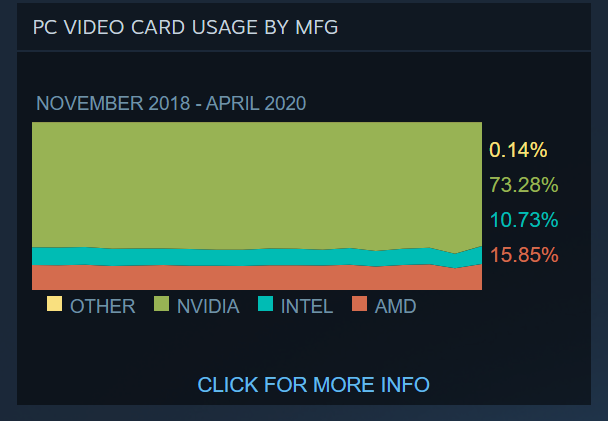
If you look closely at the graphics containing information on the video cards used by Steam users, you can see a clear change in graphics cards, which were completely flat before, occurring in March 2020. Until now, the proportions of Nvidia, Intel and AMD video cards have remained at the same level relative to each other. Since the beginning of quarantine, the share of Intel and AMD video cards has grown quite noticeably. This growth was within 2%, which might seem insignificant, until you remember that there are more than 20 million Steam users. That is, the additional number of devices with Intel and AMD graphics cards amounted to hundreds of thousands of computers. Given the specifics of video cards from different manufacturers, we can safely assume that these hundreds of thousands of devices are office laptops that arrived at home during quarantine and that people installed Steam while the boss wasn’t able to see it anyway.
Source: steampowered.com
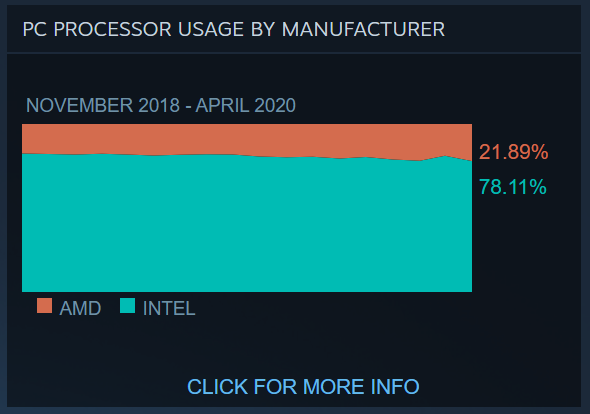
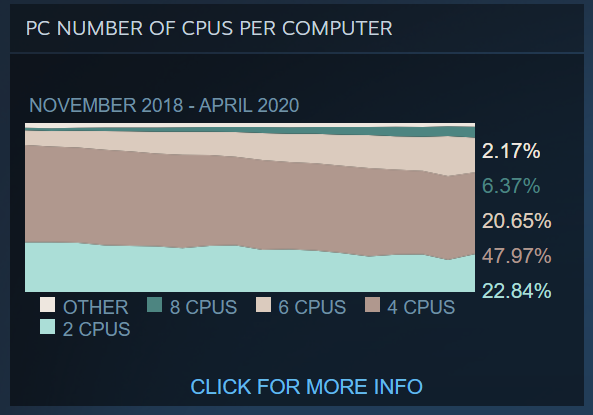
This is also confirmed by the sudden in the graphs showing the ratio of Intel and AMD processors (Intel also grew from the beginning of quarantine); and the processors used by players in terms of the number of cores (atypical growth in this proportion was shown by 4-core and 2-core processors) :
Source: steampowered.com
Let’s play with the bad guys?
The increase in the number of players and the time they spend in games, of course, did not go unnoticed by cybercriminals. Gamers have long been the target of attacks by bad guys, who are mainly interested in logins and passwords for game accounts. Now, with the connection of work computers to home networks, and, conversely, with the entry of home devices into work networks that are often poorly prepared for this, attacks on players are becoming not only a way to get to an individual user’s wallet, but also a way to access the corporate infrastructure.
In the first five months of 2020, the number of vulnerabilities discovered on Steam has already exceeded the number of vulnerabilities discovered in any of the previous years. This fact, among other things, indicates a growing interest in finding such vulnerabilities.
Source: cve.mitre.org (download)
We shouldn’t forget also that at the end of April 2020, Valve confirmed the leak of the source code of the popular network games CS: GO and Team Fortress 2. Attackers are most probably already trying to parse their code in search of vulnerabilities that can be used for their own purposes. It is important to understand that these are not offline games, but online games that need a constant connection to game servers and frequent updates. This makes their users even more vulnerable, because their devices are obviously always online, and players are always ready to install an “update” so as not to lose the ability to play.
But even without technically complex attacks using zero-day vulnerabilities, attackers have a large field for their activities. Realizing that the gaming industry is experiencing an unexpected increase in the number of players, they have “increased power” in the field of attacks that exploit the gaming theme in one way or another.
The logical step on the part of the attackers was to increase the number of phishing attacks. This is confirmed by Kaspersky AntiPhishing and the Kaspersky Security Network (KSN). By comparison with February, the number of hits on the thousand most popular phishing sites containing the word “Steam” in the name has significantly increased. Such triggering peaked in April.
An increase in the number of hits on phishing Steam-related topics relative to February 2020. Source: Kaspersky Security Network (download)
There is a clear increase in the statistics of web antivirus detections of sites with names exploiting the game theme as a whole, for example, containing the names of popular video games and gaming platforms.
The number of web attacks using game subjects during the period from January to May 2020. Source: KSN (download)
A wide variety of malicious programs are spread with such malicious links: from password stealing malware to ransomware and miners. As always, they fake free versions, updates or extensions for popular games, as well as cheat programs. A similar picture is observed among malicious files that use game-related names to stay unnoticed.
Local threats that use game-related themes as a cover
| Verdict | % of all attacks | |
| 1 | UDS: DangerousObject.Multi.Generic | 8.5% |
| 2 | Worm.Win32.Fujack.cw | 5.4% |
| 3 | PDM: Trojan.Win32.Generic | 3.8% |
| 4 | HEUR: Trojan.Multi.StartPage. b | 3.5% |
| 5 | PDM: Trojan.Win32.Bazon.a | 3.5% |
| 6 | Trojan.WinLNK.Agent.ra | 3.4% |
| 7 | HEUR: Trojan.Win32.Generic | 3.2% |
| 8 | Email-Worm.Win32. Brontok.q | 3.2% |
| 9 | HEUR: Trojan.WinLNK.Agent.gen | 2.7% |
| 10 | Trojan.WinLNK.Agent.rx | 2.3% |
The statistics do not take into account the Hacktool category of threats – tools that are usually installed by the users themselves but can be used for malicious purposes. We include remote access clients, traffic analyzers, etc. in this category. This category is of interest here because modern cheat programs often use the same techniques as malware, such as memory injection and exploiting vulnerabilities to bypass protection. If we add this kind of detection to the statistics, it will take first place with a share of 10%.
Judging by the statistics obtained from our web antivirus, the attackers focus the most on Minecraft usage. The Witcher 3: Wild Hunt also hits the TOP 3 of the most exploited games, the popularity of which has grown sharply thanks to the series based on the novels by Andrzej Sapkowski.
The number of attacks using the theme of an online game, January-May 2020. Source: KSN (download)
Following the dynamics of the responses to the links containing the names of the games, we came to the conclusion that from April to early May, the attackers conducted a campaign in which they used several games at once. In particular, Overwatch and Players Unknown Battlegrounds came into the view of our radar. If you look closely at the graph, you can see many parallel peaks. Before and after the indicated period, this trend does not persist.
Web attacks using the themes of Overwatch and PUBG, January-May 2020. Source: KSN (download)
Users in Vietnam are most susceptible to attacks using game-related topics: almost 8% of all web antivirus detections in this country occurred on sites whose names used the theme of games.
TOP 20 countries by the proportion of blocked attempts to enter malicious sites using the theme of online games, January-May 2020. Source: KSN
| Country | Percentage of attacked users |
| Vietnam | 7.90% |
| Algeria | 6.67% |
| South Korea | 6.23% |
| Hungary | 6.20% |
| Romania | 5.98% |
| Poland | 5.96% |
| Egypt | 5.20% |
| Portugal | 4.84% |
| Malaysia | 4.75% |
| Greece | 4.56% |
| Philippines | 4.51% |
| Uzbekistan | 4.48% |
| Tunisia | 4.41% |
| Morocco | 4.06% |
| Iraq | 3.82% |
| Brazil | 3.61% |
| Italy | 3.59% |
| Indonesia | 3.54% |
| Myanmar | 3.52% |
| France | 3.52% |
Following Vietnam, the TOP 5 countries for this parameter include Algeria, Korea, Hungary and Romania. In general, the TOP 20 includes many countries in North Africa, Asia and Europe, especially Southern and Eastern Europe.
Conclusion
Tens of millions of people who find themselves isolated at home (combined with plenty of free time) have given a serious boost to the gaming industry. Of course, the attackers could not help but take advantage of this situation and we have seen an impressive increase in attempts to switch to phishing sites that exploit gaming topics.
However, we should keep in mind that this was facilitated not only by the efforts of attackers, but also by the careless actions of the users themselves, who fell for fake emails apparently sent on behalf of game services, or who were looking for hacked versions of some popular games and cheat programs for others.
Unfortunately, in most cases, cybercriminals do not need technologically sophisticated schemes to carry out successful attacks. It is enough to use relevant topics, one of which in the spring of 2020 was video games.


0 Commentaires