Highly targeted spearphishing emails are being sent to oil and gas companies in hopes of infecting them with the Agent Tesla spyware.
Attackers are targeting energy companies with the Agent Tesla spyware, as seen in recent spearphishing emails with malicious attachments. Researchers say that until now, Agent Tesla has not been associated with campaigns targeting the oil-and-gas vertical.
The emails leverage the tumultuous nature of today’s oil and gas markets, which have been under tremendous stress in recent weeks, as the global COVID-19 pandemic lowered oil demand. At the same time, an agreement over oil production has been struck in a recent meeting between the OPEC+ alliance and the Group of 20 nations.
Attackers are taking advantage of the concerns around this crisis by impersonating a well-known Egyptian engineering contractor (Engineering for Petroleum and Process Industries, or Enppi), with experience in onshore and offshore projects in oil and gas, as well as a shipment company (Glory Shipping Marine Co. Ltd).
“Cybercriminals are often opportunistic and leverage popular media topics in spearphishing campaigns that usually target large numbers of victims,” said Liviu Arsene, cybersecurity researcher with Bitdefender, in a Tuesday analysis. “However, we recently found a campaign that seems to specifically target the oil & gas sector, based on a telemetry spike on March 31. Interestingly, the payload is a spyware trojan that packs keylogging capabilities, and has not been associated with oil and gas spearphishing campaigns in the past.”
The energy companies that are being targeted are located in Malaysia, the United States, Iran, South Africa, Oman and Turkey, as well as the Philippines, researchers said. Victims were mostly in oil and gas, charcoal processing, hydraulic plants, manufacturing of raw materials and transporting large merchandise.
Highly Targeted Emails
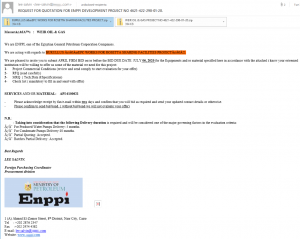
The first campaign, which ran from March 31 to April 6, mimicked Enppi, claiming to invite victims to submit a bid for equipment and materials as part of the Rosetta Sharing Facilities Project, on behalf of a well-known gas company (Burullus).
The attackers have done their research here: The Rosetta Sharing Facilities Project is a real project that is actually linked to Enppi and Burullus.
“To someone in the oil and gas industry, who has knowledge about these projects, the email and the information within might seem sufficiently convincing to open the attachments,” said Arsene.
The email, titled “REQUEST FOR QUOTATION FOR ENPPI DEVELOPMENT PROJECT NO 4621-422-298-01-20,” lists a bid submission deadline and requests a bid bond. The attached .ZIP archives purport to contain a list of requested materials and equipment; however, actually drop the spyware. These two attachments contain an executable (“BURULLUS “EPC WORKS FOR ROSETTA SHARING FACILITIES PROJECT.exe” or “WEIR OIL & GAS PROJECT NO 4621-422-298-01-20.exe”) which then drops Agent Tesla.
The spyware then goes on to collect sensitive information and different types of credentials, and sends them back to the command and control (C2) server (smtp[:]//smtp.yandex.com:587).
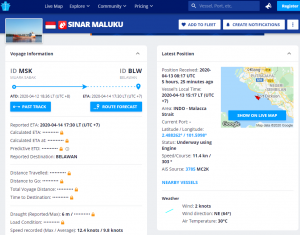
The second campaign started April 12, and purported to be from Glory Shipping Marine. The emails informed victims that they need to send an Estimated Port Disbursement Account (ERDA) for a shipping vessel, and information about container-flow management (referenced as “cfm” in the email). The email contained a malicious attachment that also executed Agent Tesla.
Again, attackers have done their homework here: The shipping vessel at the email’s heart (MT.Sinar Maluku) is legitimate, registered under the Indonesian flag. The ship had left port on April 12 and was expected to reach its destination on April 14.
“This email serves as another example of the lengths to which attackers will go to get their facts straight, make the email seem legitimate and specifically target a vertical,” researchers said.
Agent Tesla: New For Oil and Gas
Agent Tesla has been around since 2014, but has continually been updated to adopt further stealth and persistence tactics. The spyware has capabilities to extract credentials, copy clipboard data, perform screen captures, form-grabbing and keylogging functionality, and can collect credentials for a variety of installed applications.
“It reportedly operates under a malware-as-a-service offering, with its developers offering various pricing tiers based on different licensing models,” said researchers. “Agent Tesla operators seem to have stayed in business for quite some time.”
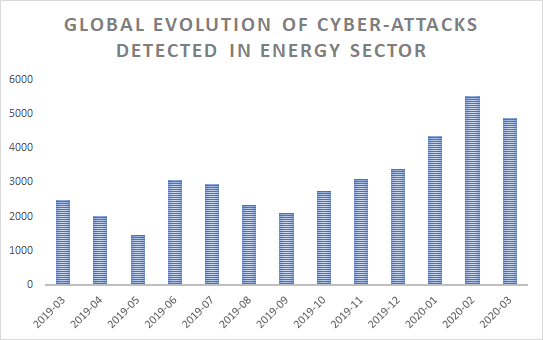
It makes sense for cybercriminals to target oil and gas given the news surrounding the industry, researchers said. While the segment has been of particular interest to cyberattackers recently, the number of malware reports targeting this industry has been increasing in early 2020.
“Starting October 2019, the global evolution of cyberattacks on the energy industry has steadily increased on a monthly basis, peaking in February 2020,” said researchers. “With over 5,000 malicious reports from companies that operate in the energy industry, cybercriminals seem to have taken a keen interest in this vertical, perhaps as it has become more important and strategic after recent oil price fluctuations.”
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.



0 Commentaires